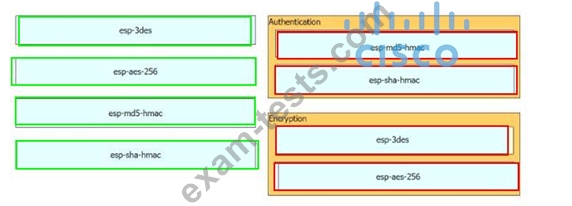
Question 106
Drag and drop the cryptographic algorithms for IPsec from the left onto the cryptographic processes on the right.


Question 107
What is the function of the Context Directory Agent?
Question 108
What provides the ability to program and monitor networks from somewhere other than the DNAC GUI?
Question 109
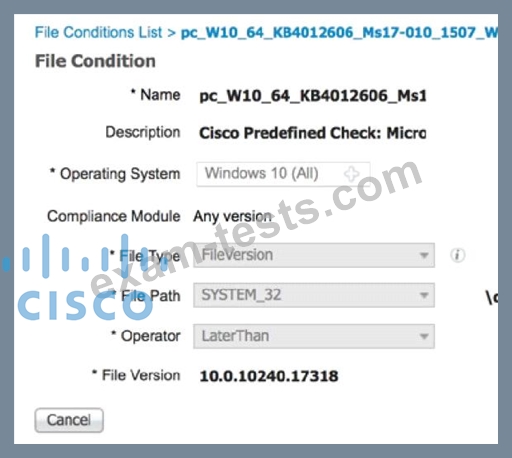
An engineer used a posture check on a Microsoft Windows endpoint and discovered that the MS17-010 patch was not installed, which left the endpoint vulnerable to WannaCry ransomware. Which two solutions mitigate the risk of this ransom ware infection? (Choose two)
Question 110
Which form of attack is launched using botnets?