Question 136
Which feature is supported when deploying Cisco ASAv within AWS public cloud?
Question 137
Which deployment model is the most secure when considering risks to cloud adoption?
Question 138
Which attack is commonly associated with C and C++ programming languages?
Question 139
Refer to the exhibit.
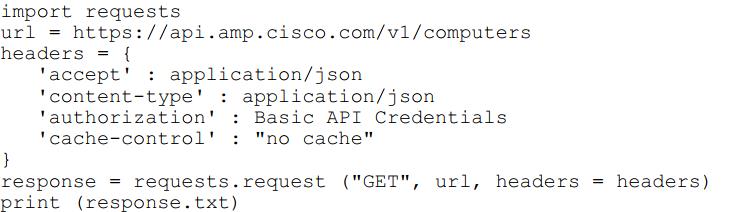
What will happen when this Python script is run?

What will happen when this Python script is run?
Question 140
Refer to the exhibit.
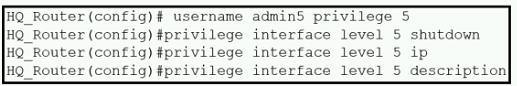
A network administrator configures command authorization for the admm5 user. What is the admin5 user able to do on HQ_Router after this configuration?

A network administrator configures command authorization for the admm5 user. What is the admin5 user able to do on HQ_Router after this configuration?

