Question 196
An engineer is trying to securely connect to a router and wants to prevent insecure algorithms from being used.
However, the connection is failing. Which action should be taken to accomplish this goal?
However, the connection is failing. Which action should be taken to accomplish this goal?
Question 197
Why is it important to patch endpoints consistently?
Question 198
Which algorithm is an NGE hash function?
Question 199
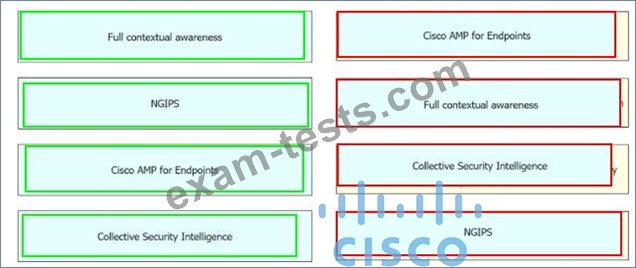
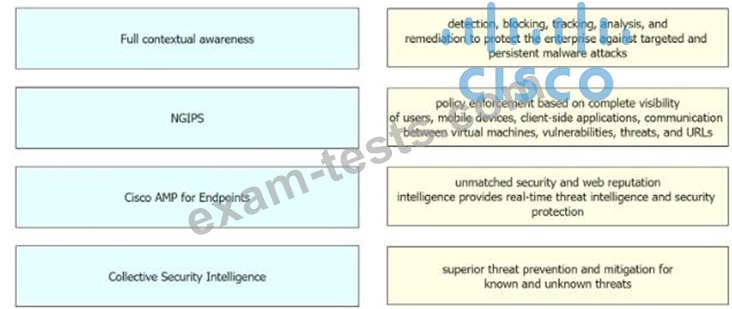
Drag and drop the security solutions from the left onto the benefits they provide on the right.

Question 200
A network administrator is configuring a switch to use Cisco ISE for 802.1X. An endpoint is failing authentication and is unable to access the network. Where should the administrator begin troubleshooting to verify the authentication details?