Question 201
Cisco SensorBase gaihers threat information from a variety of Cisco products and services and performs analytics to find patterns on threats Which term describes this process?
Question 202
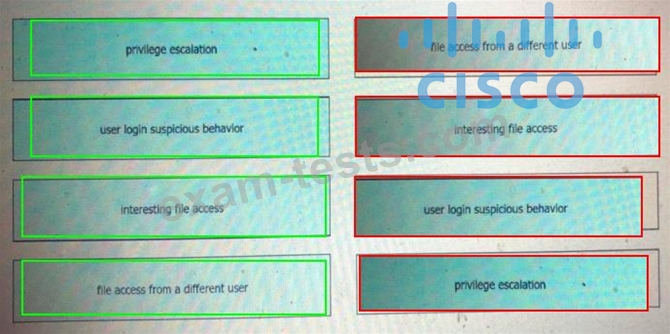
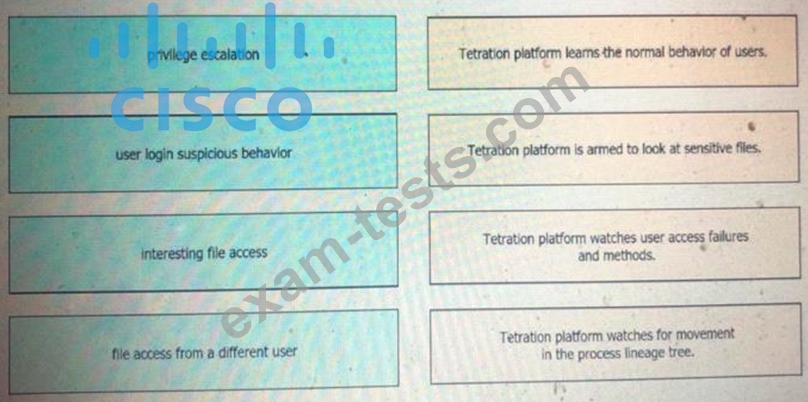
Drag and drop the suspicious patterns for the Cisco Tetration platform from the left onto the correct definitions on the right.



Question 203
A network engineer must configure a Cisco ESA to prompt users to enter two forms of information before gaining access The Cisco ESA must also join a cluster machine using preshared keys What must be configured to meet these requirements?
Question 204
Which parameter is required when configuring a Netflow exporter on a Cisco Router?
Question 205
What is the difference between Cross-site Scripting and SOL Injection attacks?