Question 426
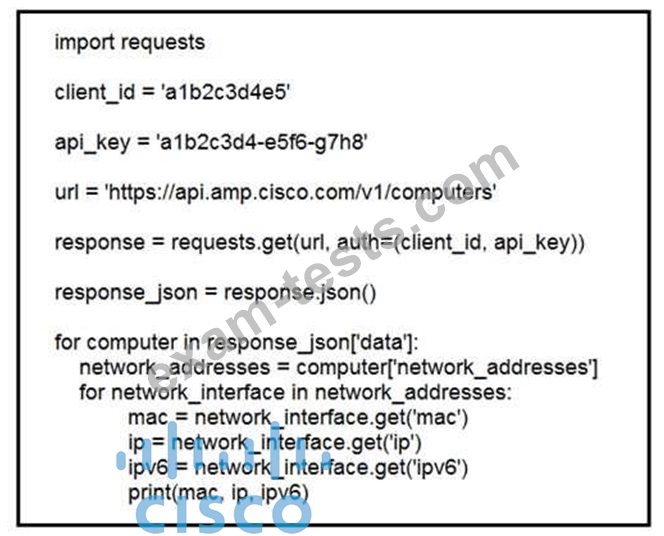
Refer to the exhibit. What does the API do when connected to a Cisco security appliance?
Question 427
What is the result of running the crypto isakmp key ciscXXXXXXXX address 172.16.0.0 command?
Question 428
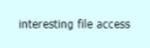
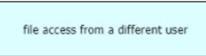
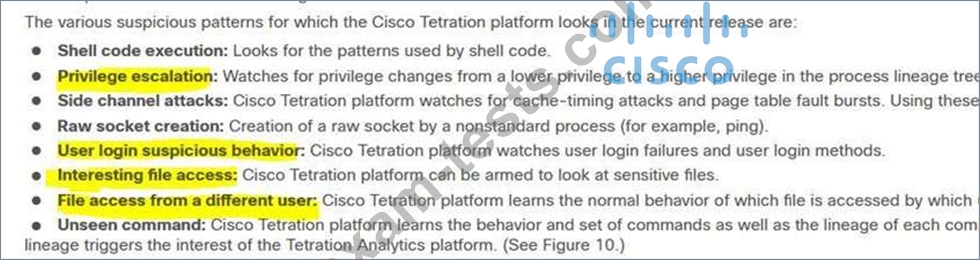
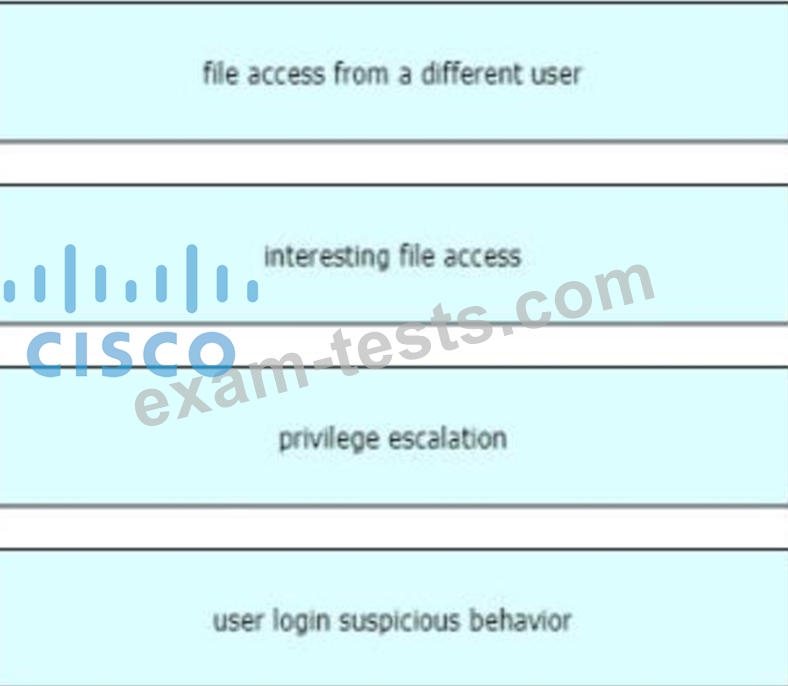
Drag and drop the suspicious patterns for the Cisco Tetration platform from the left onto the correct definitions on the right.

Question 429
An organization wants to secure users, data, and applications in the cloud. The solution must be API-based and operate as a cloud-native CASB. Which solution must be used for this implementation?
Question 430
Which proxy mode must be used on Cisco WSA to redirect TCP traffic with WCCP?