Question 241
An organization wants to provide visibility and to identify active threats in its network using a VM. The organization wants to extract metadata from network packet flow while ensuring that payloads are not retained or transferred outside the network Which solution meets these requirements?
Question 242
What is managed by Cisco Security Manager?
Question 243
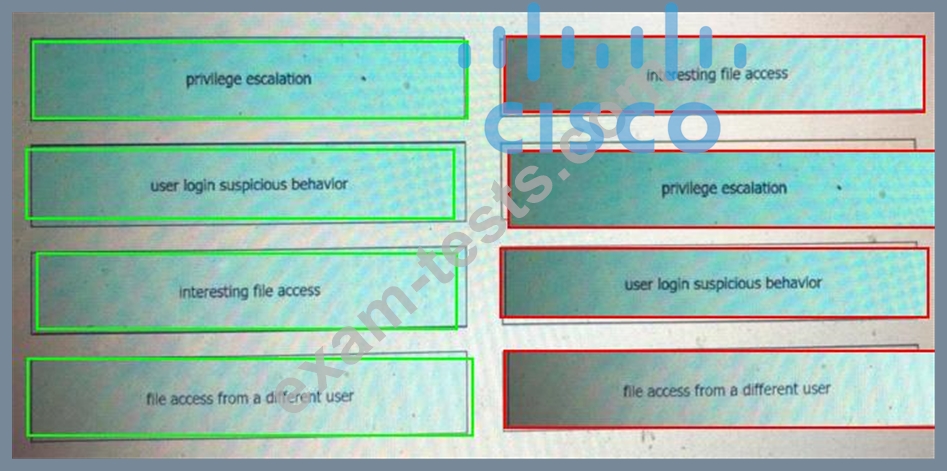
Drag and drop the suspicious patterns for the Cisco Tetration platform from the left onto the correct definitions on the right.
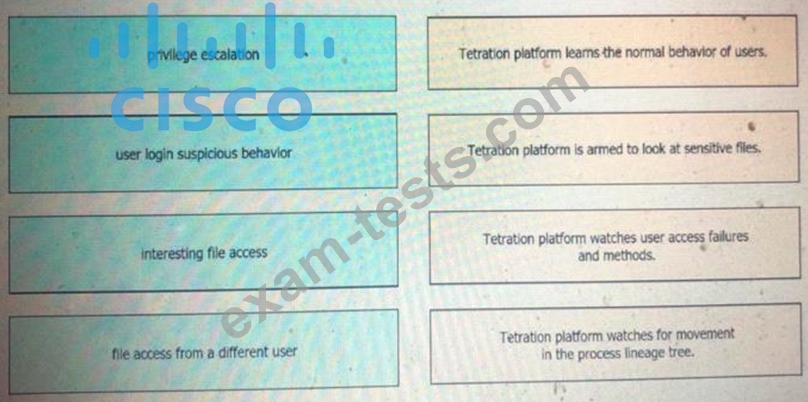

Question 244
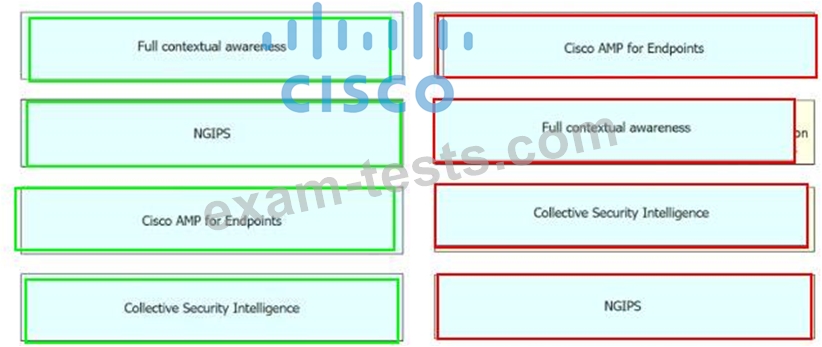
Drag and drop the security solutions from the left onto the benefits they provide on the right.
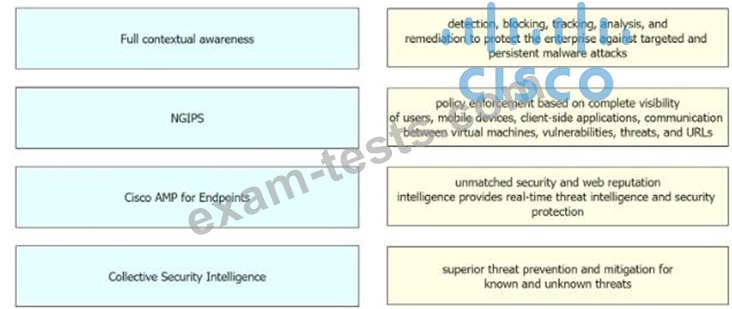

Question 245
The Cisco ASA must support TLS proxy for encrypted Cisco Unified Communications traffic.
Where must the ASA be added on the Cisco UC Manager platform?
Where must the ASA be added on the Cisco UC Manager platform?