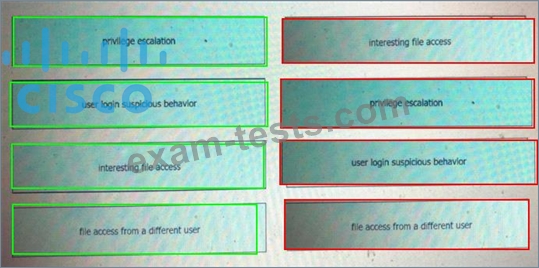
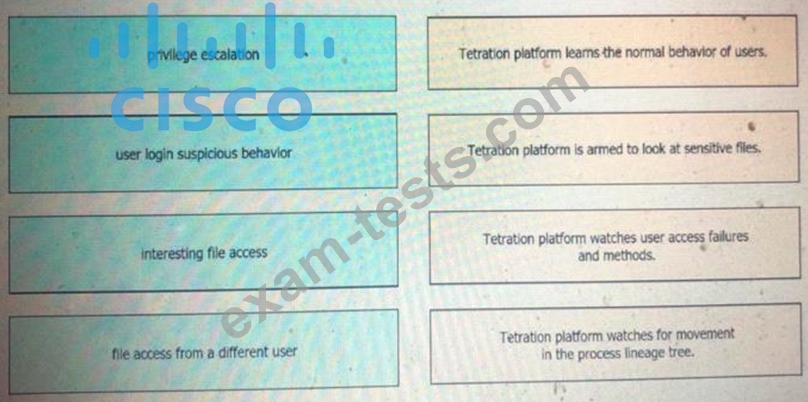
Question 261
Drag and drop the suspicious patterns for the Cisco Tetration platform from the left onto the correct definitions on the right.

Question 262
Which term describes when the Cisco Firepower downloads threat intelligence updates from Cisco Talos?
Question 263
Which flaw does an attacker leverage when exploiting SQL injection vulnerabilities?
Question 264
A Cisco ESA network administrator has been tasked to use a newly installed service to help create policy based on the reputation verdict. During testing, it is discovered that the Cisco ESA is not dropping files that have an undetermined verdict. What is causing this issue?
Question 265
An administrator wants to ensure that all endpoints are compliant before users are allowed access on the corporate network. The endpoints must have the corporate antivirus application installed and be running the latest build of Windows 10.
What must the administrator implement to ensure that all devices are compliant before they are allowed on the network?
What must the administrator implement to ensure that all devices are compliant before they are allowed on the network?