Question 271
Refer to the exhibit.
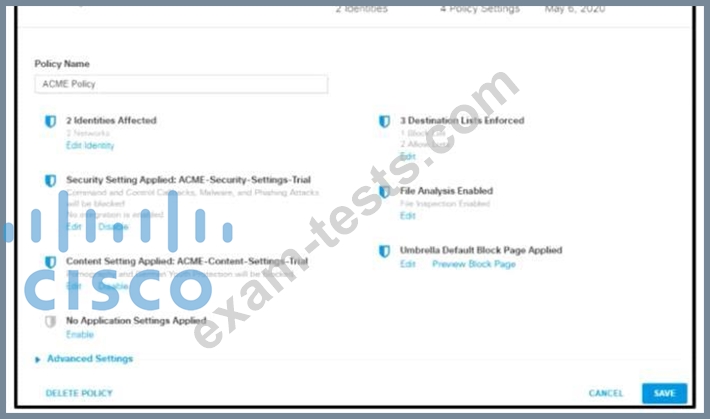
How does Cisco Umbrella manage traffic that is directed toward risky domains?

How does Cisco Umbrella manage traffic that is directed toward risky domains?
Question 272
Which security solution is used for posture assessment of the endpoints in a BYOD solution?
Question 273
Which Dos attack uses fragmented packets to crash a target machine?
Question 274
In which form of attack is alternate encoding, such as hexadecimal representation, most often observed?
Question 275
Which technology should be used to help prevent an attacker from stealing usernames and passwords of users within an organization?

