Question 336
Which two endpoint measures are used to minimize the chances of falling victim to phishing and social engineering attacks? (Choose two.)
Question 337
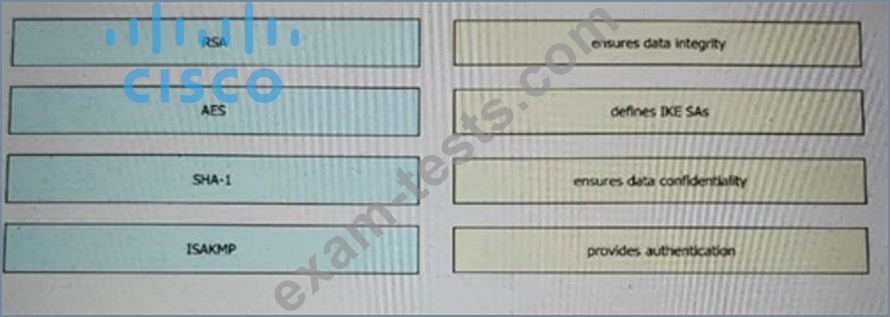
Drag and drop the VPN functions from the left onto the description on the right.

Question 338
What is a description of microsegmentation?
Question 339
What is the purpose of CA in a PKI?
Question 340
What is the role of an endpoint in protecting a user from a phishing attack?


