Question 356
Which two key and block sizes are valid for AES? (Choose two.)
Question 357
Which characteristic is unique to a Cisco WSAv as compared to a physical appliance?
Question 358
What is managed by Cisco Security Manager?
Question 359
An engineer notices traffic interruption on the network. Upon further investigation, it is learned that broadcast packets have been flooding the network. What must be configured, based on a predefined threshold, to address this issue?
Question 360
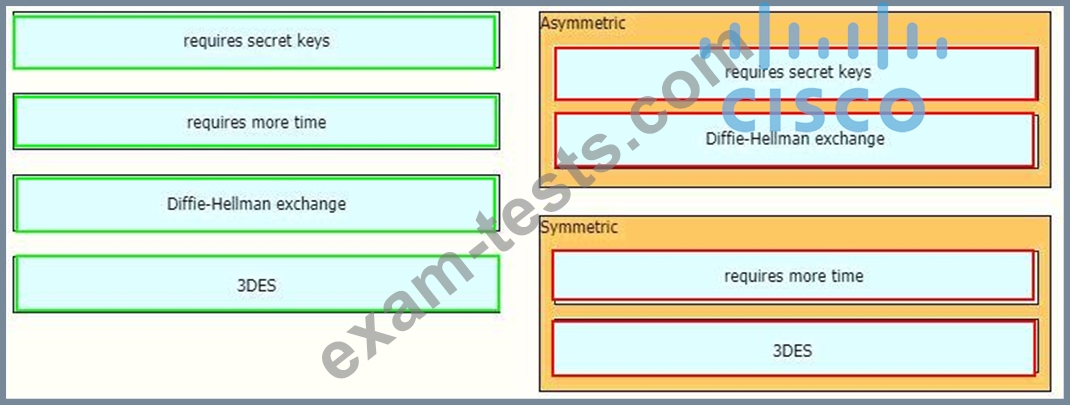
Drag and drop the descriptions from the left onto the encryption algorithms on the right.