Question 131
What is the result of running the crypto isakmp key ciscXXXXXXXX address 172.16.0.0 command?
Question 132
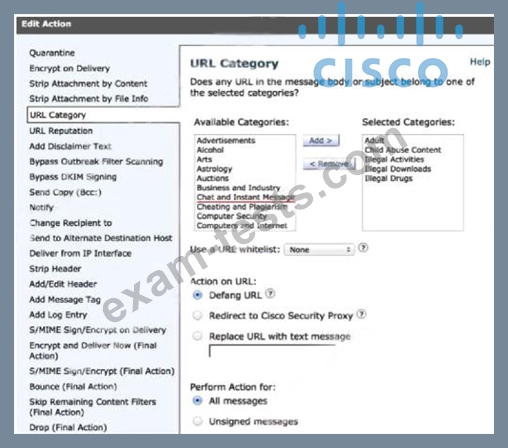
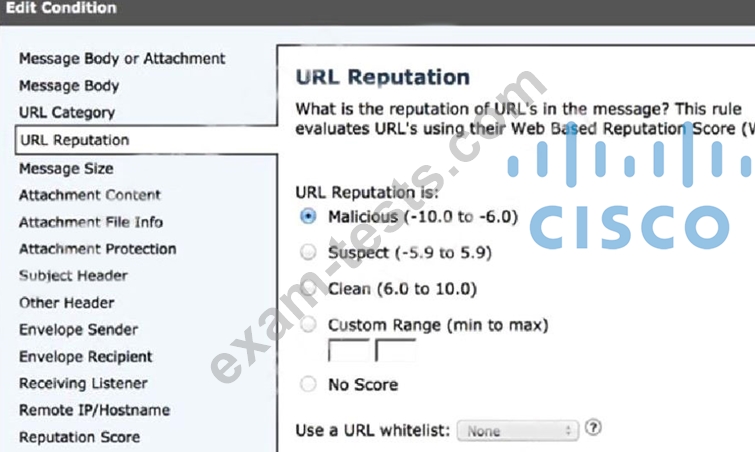
A network administrator is configuring a rule in an access control policy to block certain URLs and selects the "Chat and Instant Messaging" category. Which reputation score should be selected to accomplish this goal?
Question 133
A malicious user gained network access by spoofing printer connections that were authorized using MAB on four different switch ports at the same time. What two catalyst switch security features will prevent further violations? (Choose two)
Question 134
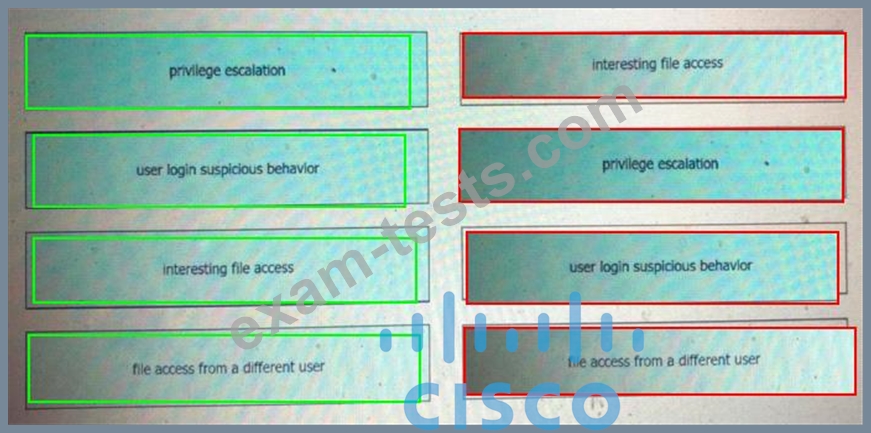
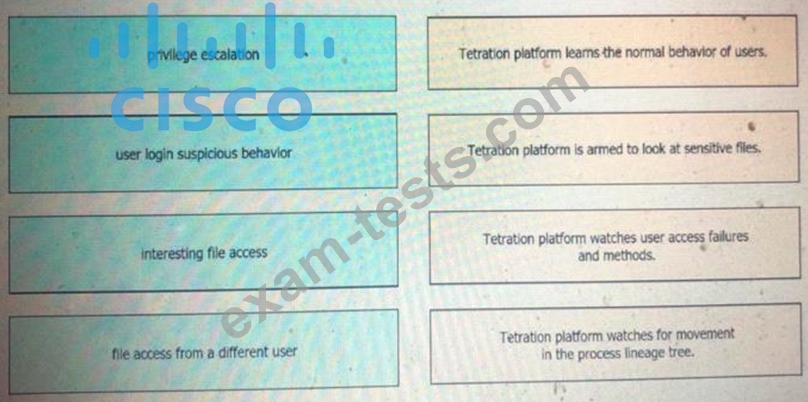
Drag and drop the suspicious patterns for the Cisco Tetration platform from the left onto the correct definitions on the right.

Question 135
Which type of protection encrypts RSA keys when they are exported and imported?