Question 141
Which two risks is a company vulnerable to if it does not have a well-established patching solution for endpoints? (Choose two.)
Question 142
Which method is used to deploy certificates and configure the supplicant on mobile devices to gain access to network resources?
Question 143
How is DNS tunneling used to exfiltrate data out of a corporate network?
Question 144
Refer to the exhibit.
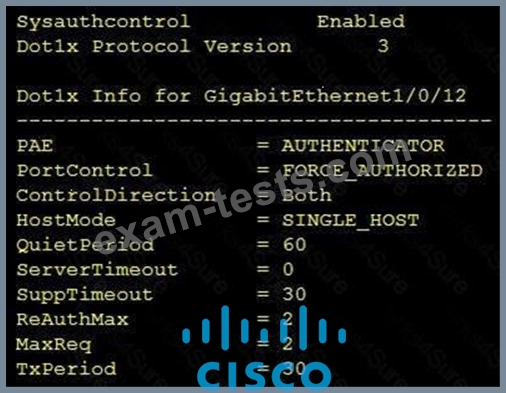
Which command was used to display this output?

Which command was used to display this output?
Question 145
Which policy represents a shared set of features or parameters that define the aspects of a managed device that are likely to be similar to other managed devices in a deployment?


