Question 166
Refer to the exhibit.
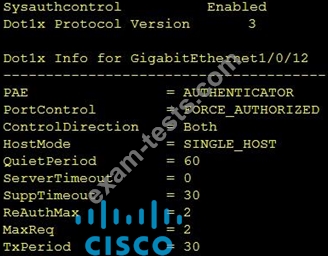
Which command was used to display this output?

Which command was used to display this output?
Question 167
What is the term for having information about threats and threat actors that helps mitigate harmful events that would otherwise compromise networks or systems?
Question 168
After a recent breach, an organization determined that phishing was used to gain initial access to the network before regaining persistence. The information gained from the phishing attack was a result of users visiting known malicious websites. What must be done in order to prevent this from happening in the future?
Question 169
Which security solution protects users leveraging DNS-layer security?
Question 170
Which attribute has the ability to change during the RADIUS CoA?