Question 351
What are the two most commonly used authentication factors in multifactor authentication? (Choose two.)


Question 352
An organization has DHCP servers set up to allocate IP addresses to clients on the LAN. What must be done to ensure the LAN switches prevent malicious DHCP traffic while also distributing IP addresses to the correct endpoints?
Question 353
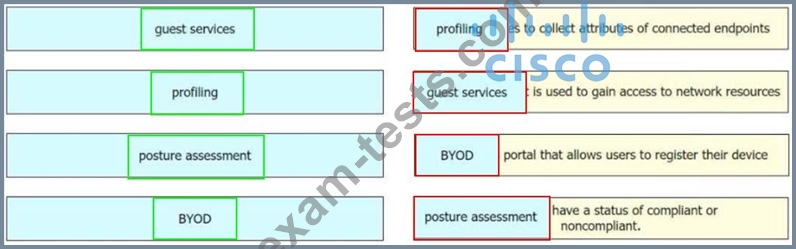
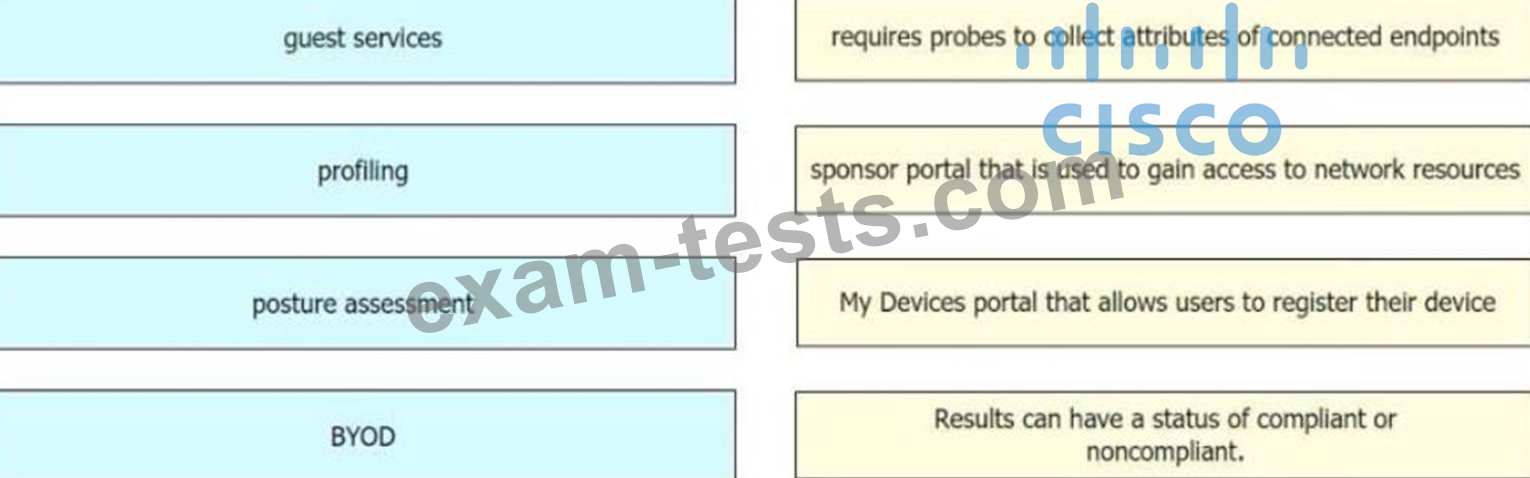
Drag and drop the concepts from the left onto the correct descriptions on the right

Question 354
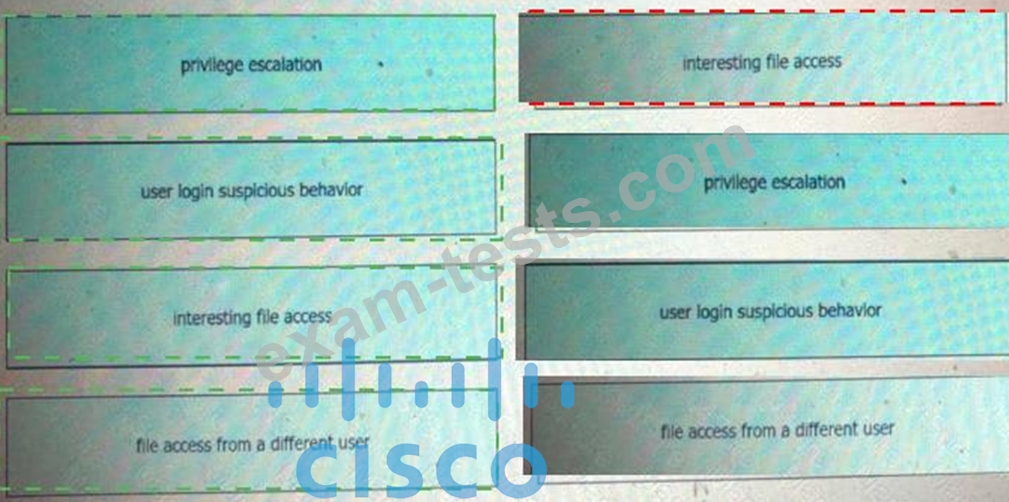
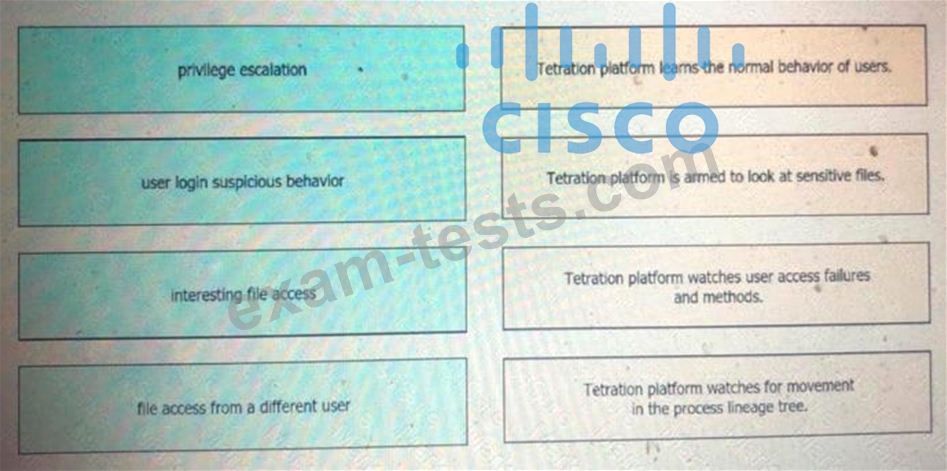
Drag and drop the suspicious patterns for the Cisco Tetration platform from the left onto the correct definitions on the right.

Question 355
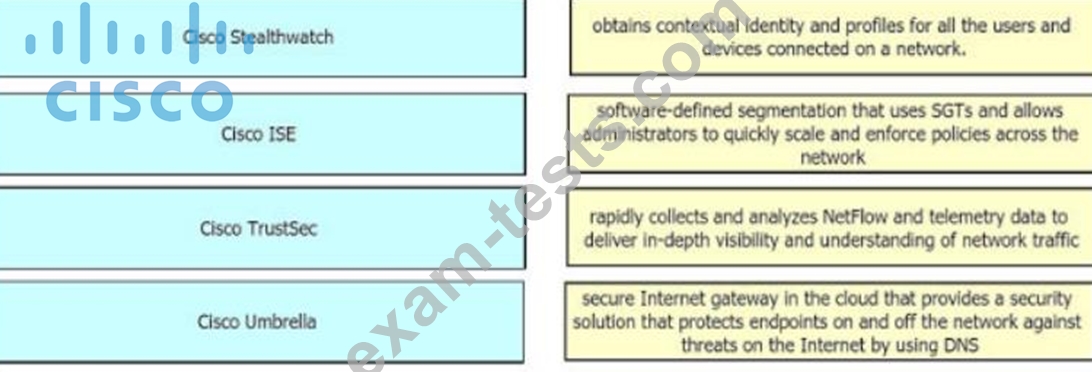
Drag and drop the solutions from the left onto the solution's benefits on the right.