Question 346
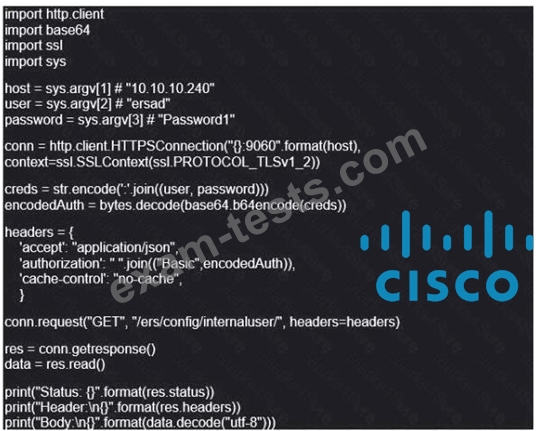
Refer to the exhibit. What does this Python script accomplish?
Question 347
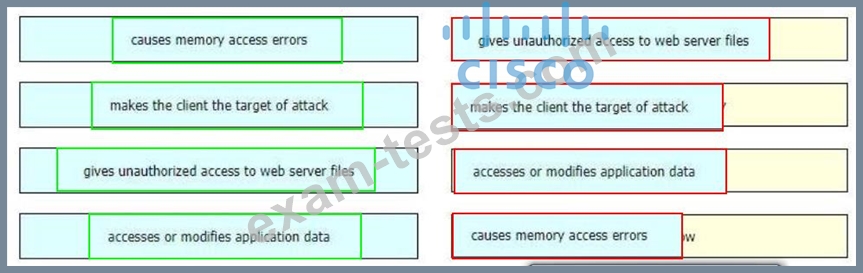
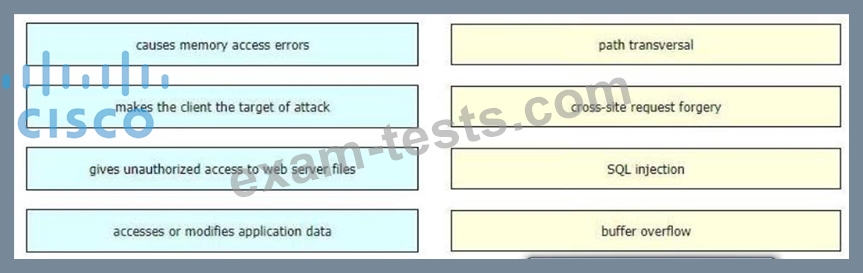
Drag and drop the exploits from the left onto the type of security vulnerability on the right.

Question 348
An organization is implementing AAA for their users. They need to ensure that authorization is verified for every command that is being entered by the network administrator. Which protocol must be configured in order to provide this capability?
Question 349
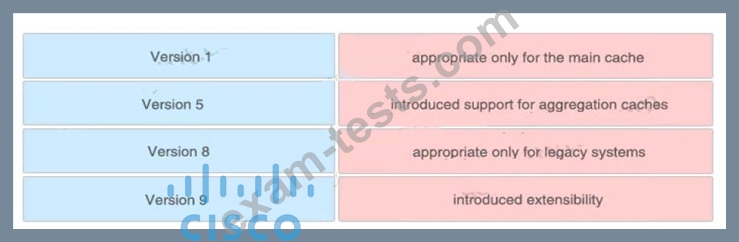
Drag and drop the NetFlow export formats from the left onto the descriptions on the right.

Question 350
Refer to the exhibit.
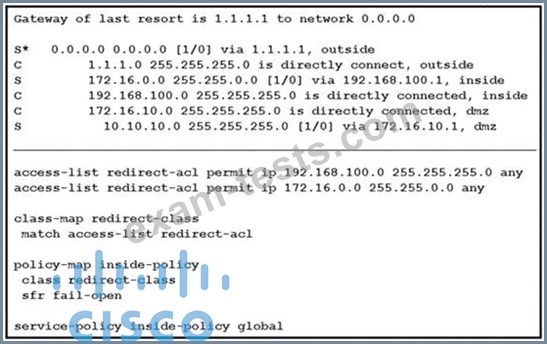
What is a result of the configuration?

What is a result of the configuration?