Question 481
Which RADIUS attribute can you use to filter MAB requests in an 802.1x deployment?
Question 482
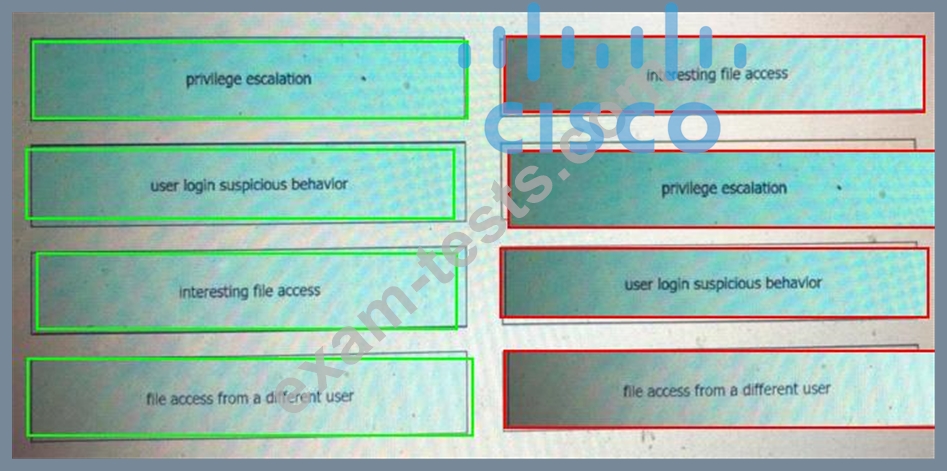
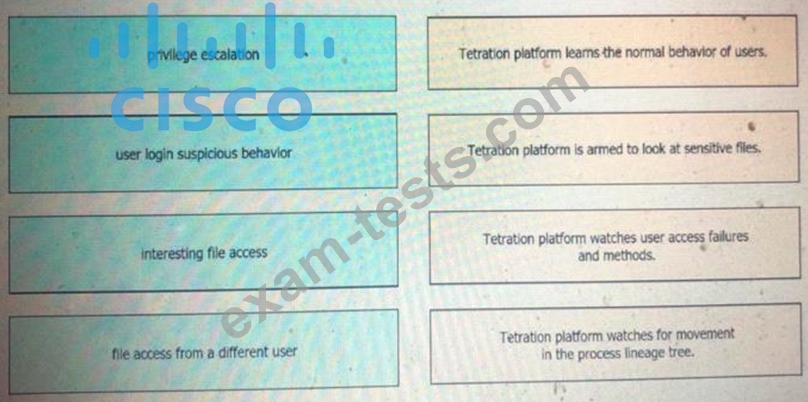
Drag and drop the suspicious patterns for the Cisco Tetration platform from the left onto the correct definitions on the right.

Question 483
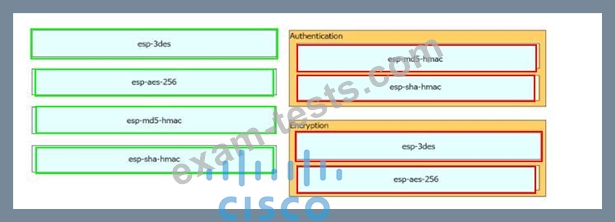
Drag and drop the cryptographic algorithms for IPsec from the left onto the cryptographic processes on the right.


Question 484
What is a functional difference between Cisco Secure Endpoint and Cisco Umbrella Roaming Client?
Question 485
A network engineer is configuring DMVPN and entered the crypto isakmp key cisc0380739941 address 0.0.0.0 command on host A.
The tunnel is not being established to hostB. What action is needed to authenticate the VPN?
The tunnel is not being established to hostB. What action is needed to authenticate the VPN?