Question 501
An engineer needs behavioral analysis to detect malicious activity on the hosts, and is configuring the organization's public cloud to send telemetry using the cloud provider's mechanisms to a security device. Which mechanism should the engineer configure to accomplish this goal?
Question 502
Which baseline form of telemetry is recommended for network infrastructure devices?
Question 503
How does Cisco Workload Optimization portion of the network do EPP solutions solely performance issues?
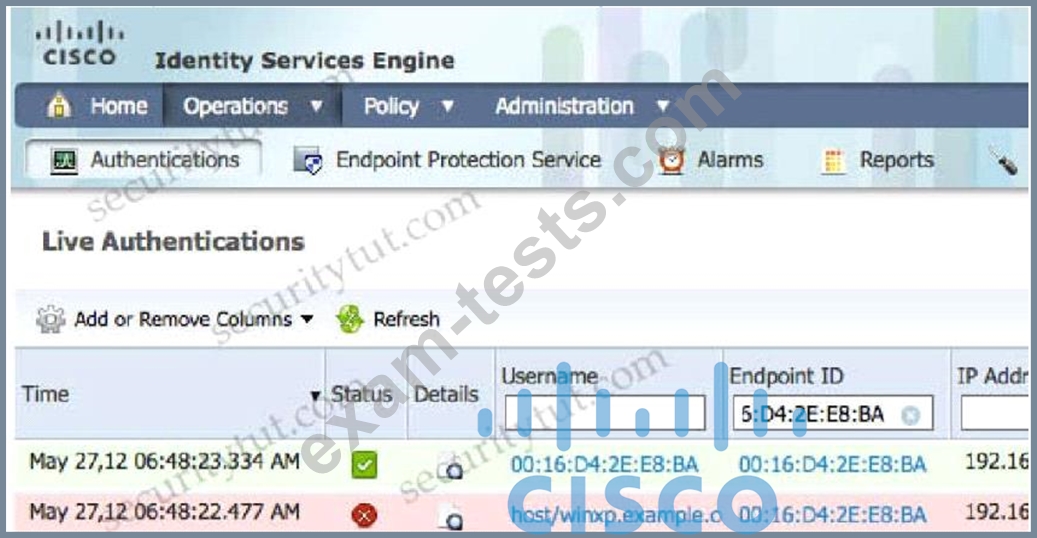
Question 504
A network administrator is configuring a switch to use Cisco ISE for 802.1X. An endpoint is failing authentication and is unable to access the network. Where should the administrator begin troubleshooting to verify the authentication details?
Question 505
What is a benefit of using Cisco Tetration?