Question 156
You have been tasked with designing a data center interconnect to provide business continuity. You want to encrypt the traffic over the DCI using IEEE 802.1AE MACsec to prevent the deployment of any firewall or IPS. Which two interconnect technologies support MACsec? (Choose two.)
Question 157
What are two base components of both a source-based remotely triggered black hole and a destination- based remotely triggered black hole filtering solution? (Choose two.)
Question 158
As a part of a network design, you should tighten security to prevent man-in-the-middle.
Which two security options ensure that authorized ARP responses take place according to know IP-to-MAC address mapping? (Choose two)
Which two security options ensure that authorized ARP responses take place according to know IP-to-MAC address mapping? (Choose two)
Question 159
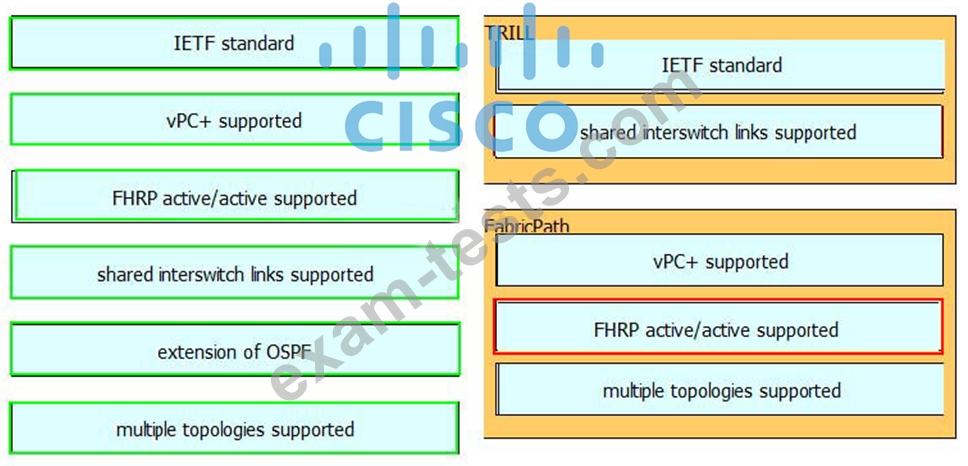
DRAG DROP
Drag and drop the technology details or features support on the left into the corresponding Layer 2 multipath technologies on the right. Not all options will be used.
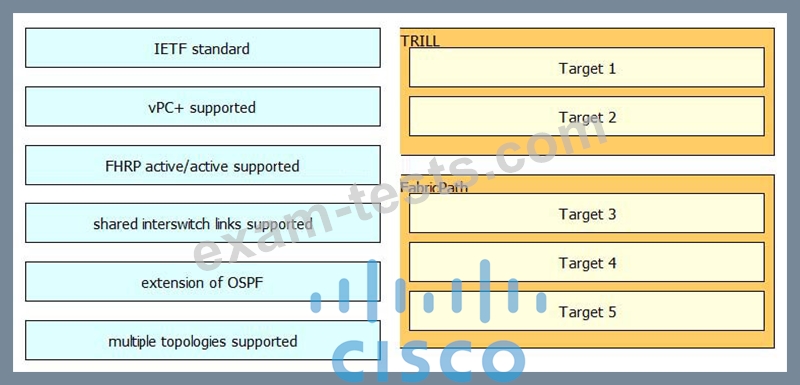
Drag and drop the technology details or features support on the left into the corresponding Layer 2 multipath technologies on the right. Not all options will be used.

Question 160
Which resource does a TCP SYN flood attack target?