Question 21
HOTSPOT
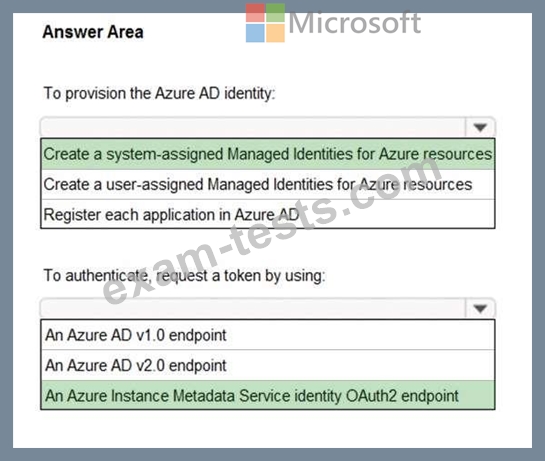
You have five .NET Core applications that run on 10 Azure virtual machines in the same subscription.
You need to recommend a solution to ensure that the applications can authenticate by using the same Azure Active Directory (Azure AD) identity. The solution must meet the following requirements:
* Ensure that the applications can authenticate only when running on the 10 virtual machines.
* Minimize administrative effort.
What should you include in the recommendation? To answer, select the appropriate options in the answer area.
Hot Area:
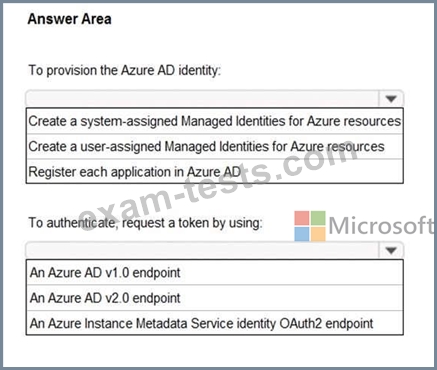
You have five .NET Core applications that run on 10 Azure virtual machines in the same subscription.
You need to recommend a solution to ensure that the applications can authenticate by using the same Azure Active Directory (Azure AD) identity. The solution must meet the following requirements:
* Ensure that the applications can authenticate only when running on the 10 virtual machines.
* Minimize administrative effort.
What should you include in the recommendation? To answer, select the appropriate options in the answer area.
Hot Area:

Question 22
You are designing an order processing system in Azure that will contain the Azure resources shown in the following table.

Which type of resource should you recommend for the integration component?

Which type of resource should you recommend for the integration component?
Question 23
You have an Azure Active Directory (Azure AD) tenant named Contoso.com. The tenant contains a group named Group1. Group1 contains all the administrator user accounts.
You discover several login attempts to the Azure portal from countries administrator users do NOT work.
You need to ensure that all login attempts to the portal from those countries require Azure Multi-Factor Authentication (MFA).
Solution: You implement an access package.
Does this meet the goal?
You discover several login attempts to the Azure portal from countries administrator users do NOT work.
You need to ensure that all login attempts to the portal from those countries require Azure Multi-Factor Authentication (MFA).
Solution: You implement an access package.
Does this meet the goal?
Question 24
You have an Azure subscription. The subscription contains Azure virtual machines that run Windows Server 2016 and Linux.
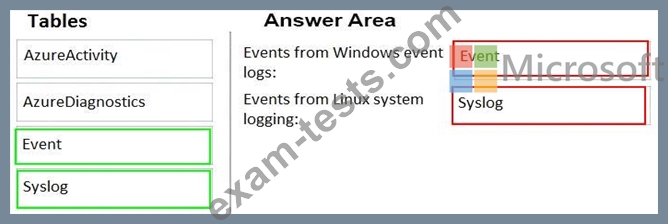
You need to use Azure Log Analytics design an alerting strategy for security-related events.
Which Log Analytics tables should you query? To answer, drag the appropriate tables to the correct log types. Each value may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.

You need to use Azure Log Analytics design an alerting strategy for security-related events.
Which Log Analytics tables should you query? To answer, drag the appropriate tables to the correct log types. Each value may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.

Question 25
Your company has the infrastructure shown in the following table.
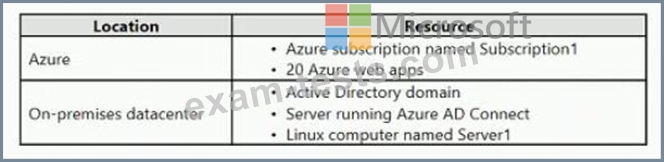
The on-premises Active Directory domain syncs to Azure Active Directory (Azure AD).
Server1 runs an application named Appl that uses LDAP queries to verify user identities in the on-premises Active Directory domain.
You plan to migrate Server1 to a virtual machine in Subscription1.
A company security policy states that the virtual machines and services deployed to Subscription1 must be prevented from accessing the on-premises network.
You need to recommend a solution to ensure that Appl continues to function after the migration. The solution must meet the security policy.
What should you include in the recommendation?

The on-premises Active Directory domain syncs to Azure Active Directory (Azure AD).
Server1 runs an application named Appl that uses LDAP queries to verify user identities in the on-premises Active Directory domain.
You plan to migrate Server1 to a virtual machine in Subscription1.
A company security policy states that the virtual machines and services deployed to Subscription1 must be prevented from accessing the on-premises network.
You need to recommend a solution to ensure that Appl continues to function after the migration. The solution must meet the security policy.
What should you include in the recommendation?