Question 26
Your company has the infrastructure shown in the following table.
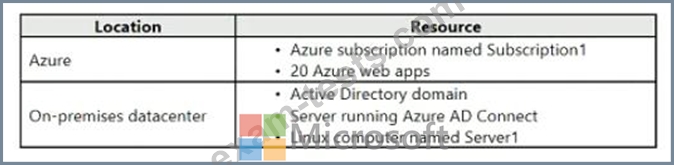
The on-premises Active Directory domain syncs to Azure Active Directory (Azure AD).
Server1 runs an application named Appl that uses LDAP queries to verify user identities in the on-premises Active Directory domain.
You plan to migrate Server1 to a virtual machine in Subscription1.
A company security policy states that the virtual machines and services deployed to Subscription! must be prevented from accessing the on-premises network.
You need to recommend a solution to ensure that Appl continues to function after the migration. The solution must meet the security policy.
What should you include in the recommendation?

The on-premises Active Directory domain syncs to Azure Active Directory (Azure AD).
Server1 runs an application named Appl that uses LDAP queries to verify user identities in the on-premises Active Directory domain.
You plan to migrate Server1 to a virtual machine in Subscription1.
A company security policy states that the virtual machines and services deployed to Subscription! must be prevented from accessing the on-premises network.
You need to recommend a solution to ensure that Appl continues to function after the migration. The solution must meet the security policy.
What should you include in the recommendation?
Question 27
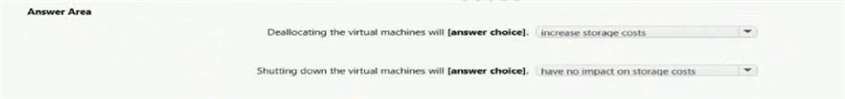
You are reviewing the budget for Azure Storage as shown in the exhibit (Click the Exhibit tab.) All the virtual machines in the Azure subscription use Premium storage.
Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
NOTE: correct selection is worth one point.

Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
NOTE: correct selection is worth one point.

Question 28
You are designing an Azure resource deployment that will use Azure Resource Manager templates. The deployment will use Azure Key Vault to store secrets.
You need to recommend a solution to meet the following requirements:
Prevent the IT staff that will perform the deployment from retrieving the secrets directly from Key Vault.
Use the principle of least privilege.
Which two actions should you recommend? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
You need to recommend a solution to meet the following requirements:
Prevent the IT staff that will perform the deployment from retrieving the secrets directly from Key Vault.
Use the principle of least privilege.
Which two actions should you recommend? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
Question 29
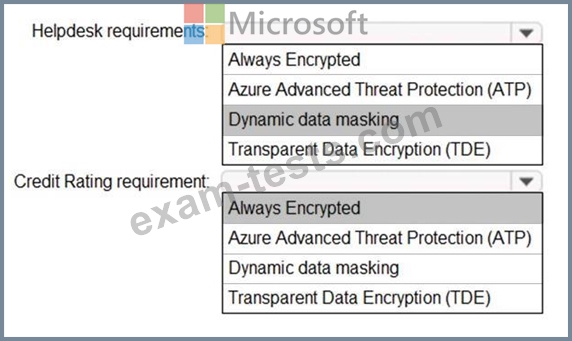
You have an Azure SQL database named DB1.
You need to recommend a data security solution for DB1. the solution must meet the following requirements:
* When helpdesk supervisors query DS1. they must see the full number of each credit card.
* When helpdesk operators Query DB1. they must see only the last four digits of each credit card number
* A column named Credit Rating must never appear in plain text within the database system, and only client applications must be able to decrypt the Credit Rating column.
What should you include in the recommendation To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

You need to recommend a data security solution for DB1. the solution must meet the following requirements:
* When helpdesk supervisors query DS1. they must see the full number of each credit card.
* When helpdesk operators Query DB1. they must see only the last four digits of each credit card number
* A column named Credit Rating must never appear in plain text within the database system, and only client applications must be able to decrypt the Credit Rating column.
What should you include in the recommendation To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

Question 30
You need to recommend a notification solution for the IT Support distribution group.
What should you include in the recommendation?
What should you include in the recommendation?