Question 106
An administrator attempts to install the package "named.9.3.6-12-x86_64.rpm" on a server.
Even though the package was downloaded from the official repository, the server states the package cannot be installed because no GPG key is found.
Which of the following should the administrator perform to allow the program to be installed?
Even though the package was downloaded from the official repository, the server states the package cannot be installed because no GPG key is found.
Which of the following should the administrator perform to allow the program to be installed?
Question 107
A Chief Information Security Officer (CISO) recently changed jobs into a new industry. The CISO's first task is to write a new, relevant risk assessment for the organization. Which of the following would BEST help the CISO find relevant risks to the organization? (Choose two.)
Question 108
A security engineer is performing an assessment again for a company. The security engineer examines the following output from the review:
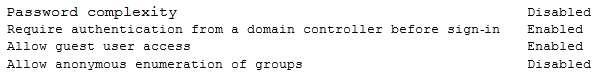
Which of the following tools is the engineer utilizing to perform this assessment?

Which of the following tools is the engineer utilizing to perform this assessment?
Question 109
A company is developing requirements for a customized OS build that will be used in an embedded environment. The company procured hardware that is capable of reducing the likelihood of successful buffer overruns while executables are processing. Which of the following capabilities must be included for the OS to take advantage of this critical hardware-based countermeasure?
Question 110
During a security event investigation, a junior analyst fails to create an image of a server's hard drive before removing the drive and sending it to the forensics analyst. Later, the evidence from the analysis is not usable in the prosecution of the attackers due to the uncertainty of tampering.
Which of the following should the junior analyst have followed?
Which of the following should the junior analyst have followed?

