Question 126
A Chief Financial Officer (CFO) has raised concerns with the Chief Information Security Officer (CISO) because money has been spent on IT security infrastructure, but corporate assets are still found to be vulnerable. The business recently funded a patch management product and SOE hardening initiative. A third party auditor reported findings against the business because some systems were missing patches. Which of the following statements BEST describes this situation?
Question 127
The Chief Information Security Officer (CISO) of an organization is concerned with the transmission of cleartext authentication information across the enterprise. A security assessment has been performed and has identified the use of ports 80. 389. and 3268. Which of the following solutions would BEST address the CISO's concerns?
Question 128
A newly hired systems administrator is trying to connect a new and fully updated, but very customized,
Android device to access corporate resources. However, the MDM enrollment process continually fails.
The administrator asks a security team member to look into the issue. Which of the following is the MOST
likely reason the MDM is not allowing enrollment?
Android device to access corporate resources. However, the MDM enrollment process continually fails.
The administrator asks a security team member to look into the issue. Which of the following is the MOST
likely reason the MDM is not allowing enrollment?
Question 129
A security appliance vendor is reviewing an RFP that is requesting solutions for the defense of a set of web-based applications. This RFP is from a financial institution with very strict performance requirements.
The vendor would like to respond with its solutions.
Before responding, which of the following factors is MOST likely to have an adverse effect on the vendor's qualifications?
The vendor would like to respond with its solutions.
Before responding, which of the following factors is MOST likely to have an adverse effect on the vendor's qualifications?
Question 130
When reviewing KRIs of the email security appliance with the Chief Information Security Officer (CISO) of an insurance company, the security engineer notices the following:
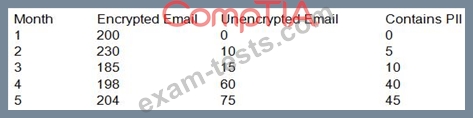
Which of the following measures should the security engineer take to ensure PII is not intercepted in transit while also preventing interruption to business?

Which of the following measures should the security engineer take to ensure PII is not intercepted in transit while also preventing interruption to business?

