Question 41
An internal penetration tester was assessing a recruiting page for potential issues before it was pushed to the production website. The penetration tester discovers an issue that must be corrected before the page goes live. The web host administrator collects the log files below and gives them to the development team so improvements can be made to the security design of the website.
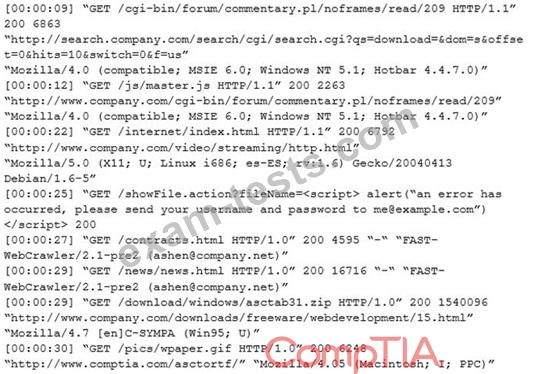
Which of the following types of attack vector did the penetration tester use?

Which of the following types of attack vector did the penetration tester use?
Question 42
A security engineer is analyzing an application during a security assessment to ensure it is configured to protect against common threats. Given the output below:
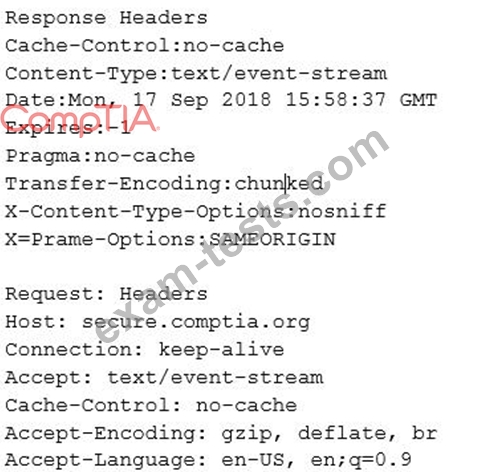
Which of the following tools did the security engineer MOST likely use to generate this output?

Which of the following tools did the security engineer MOST likely use to generate this output?
Question 43
A product owner is reviewing the output of a web-application penetration test and has identified an application that is presenting sensitive information in cleartext on a page. Which of the following code snippets would be BEST to use to remediate the vulnerability?
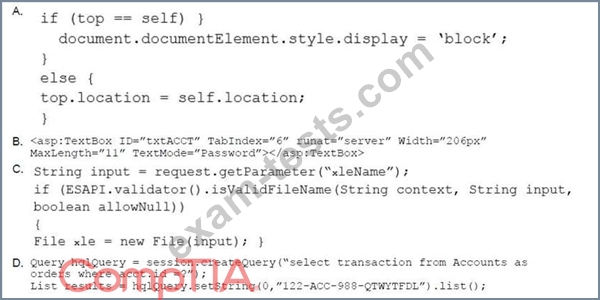

Question 44
Which of the following may indicate a configuration item has reached end-of-life?
Question 45
An attacker has been compromising banking institution targets across a regional area. The Chief Information Security Officer (CISO) at a local bank wants to detect and prevent an attack before the bank becomes a victim. Which of the following actions should the CISO take?

