Question 126
A security architect is designing a system to satisfy user demand for reduced transaction time, increased security and message integrity, and improved cryptographic security. The resultant system will be used in an environment with a broad user base where many asynchronous transactions occur every minute and must be publicly verifiable.
Which of the following solutions BEST meets all of the architect's objectives?
Which of the following solutions BEST meets all of the architect's objectives?
Question 127
A Chief Security Officer (CSO) is reviewing the organization's incident response report from a recent incident. The details of the event indicate:
A user received a phishing email that appeared to be a report from the organization's CRM tool.
The user attempted to access the CRM tool via a fraudulent web page but was unable to access the tool.
The user, unaware of the compromised account, did not report the incident and continued to use the CRM tool with the original credentials.
Several weeks later, the user reported anomalous activity within the CRM tool.
Following an investigation, it was determined the account was compromised and an attacker in another country has gained access to the CRM tool.
Following identification of corrupted data and successful recovery from the incident, a lessons learned activity was to be led by the CSO.
Which of the following would MOST likely have allowed the user to more quickly identify the unauthorized use of credentials by the attacker?
A user received a phishing email that appeared to be a report from the organization's CRM tool.
The user attempted to access the CRM tool via a fraudulent web page but was unable to access the tool.
The user, unaware of the compromised account, did not report the incident and continued to use the CRM tool with the original credentials.
Several weeks later, the user reported anomalous activity within the CRM tool.
Following an investigation, it was determined the account was compromised and an attacker in another country has gained access to the CRM tool.
Following identification of corrupted data and successful recovery from the incident, a lessons learned activity was to be led by the CSO.
Which of the following would MOST likely have allowed the user to more quickly identify the unauthorized use of credentials by the attacker?
Question 128
An administrator is working with management to develop policies related to the use of the cloud-based resources that contain corporate dat a. Management plans to require some control over organizational data stored on personal devices, such as tablets. Which of the following controls would BEST support management's policy?
Question 129
A corporate forensic investigator has been asked to acquire five forensic images of an employee database application. There are three images to capture in the United States, one in the United Kingdom, and one in Germany. Upon completing the work, the forensics investigator saves the images to a local workstation. Which of the following types of concerns should the forensic investigator have about this work assignment?
Question 130
After analyzing code, two developers al a company bring these samples to the security operations manager.
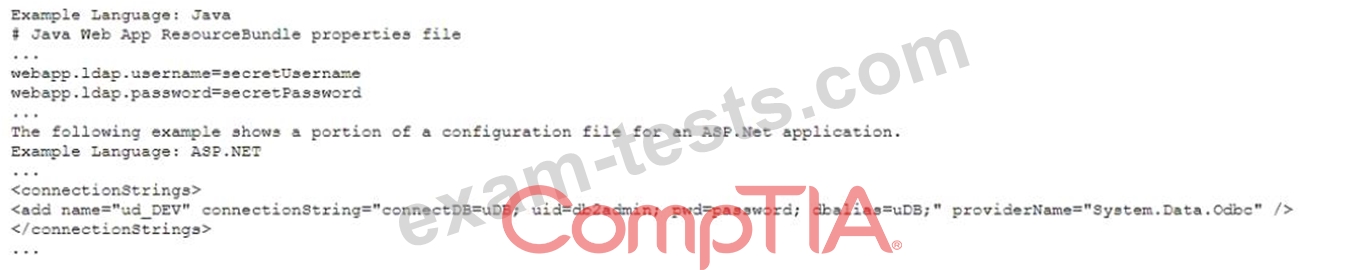
Which of the following would BEST solve these coding problems?

Which of the following would BEST solve these coding problems?

