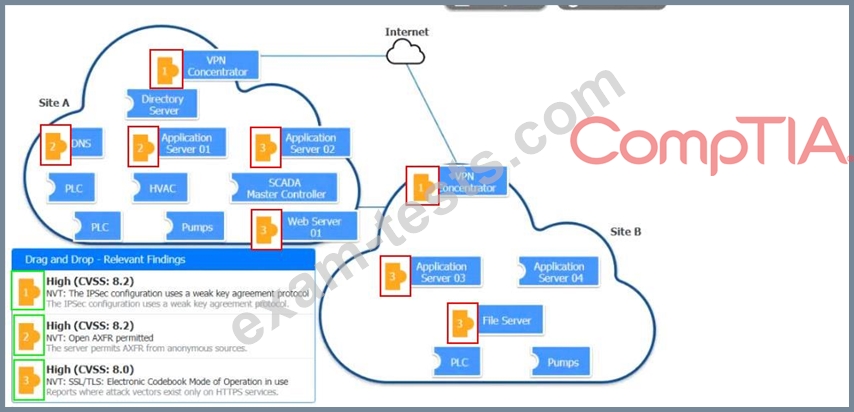
Question 101
A vulnerability scan with the latest definitions was performed across Sites A and B.
Match each relevant finding to the affected host-After associating the finding with the appropriate host(s), click the host to select the appropriate corrective action for that finding.
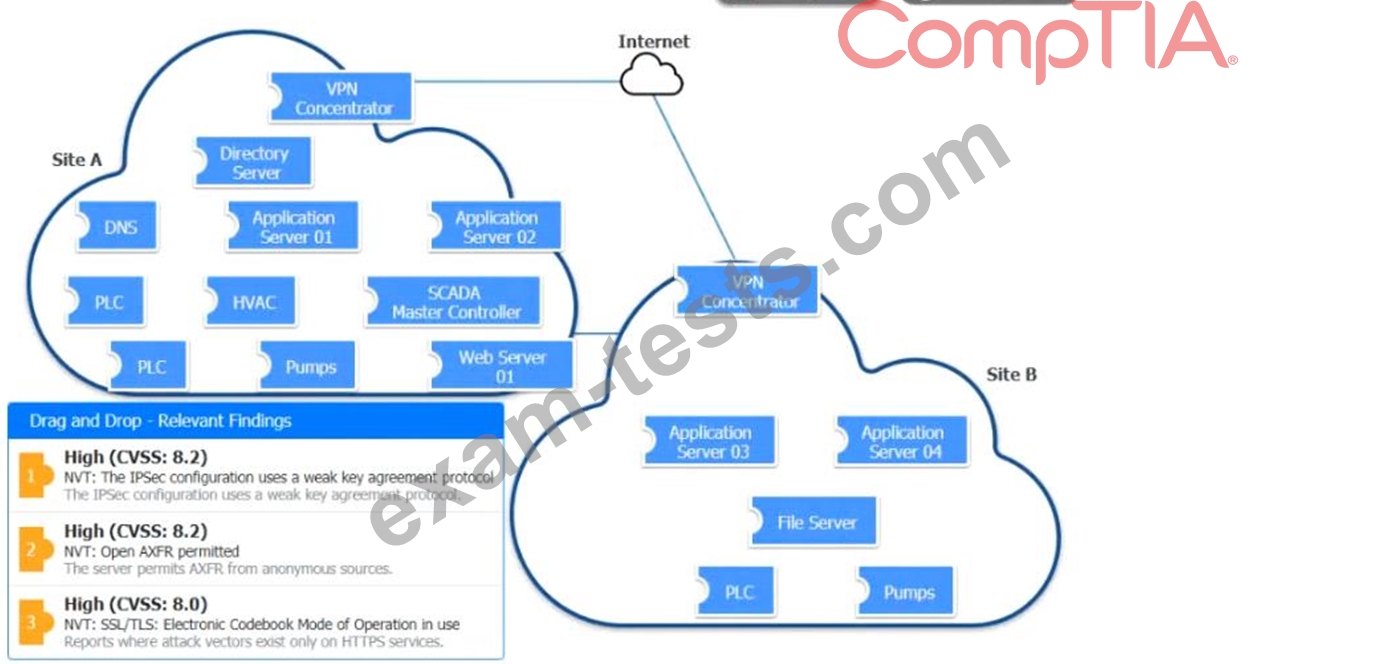
Match each relevant finding to the affected host-After associating the finding with the appropriate host(s), click the host to select the appropriate corrective action for that finding.

Question 102
A cybersecurity analyst created the following tables to help determine the maximum budget amount the business can justify spending on an improved email filtering system:
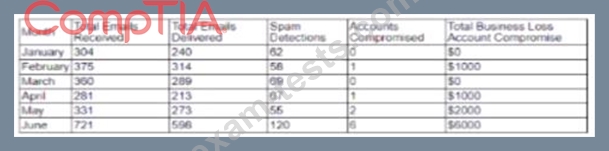

Which of the following meets the budget needs of the business?


Which of the following meets the budget needs of the business?
Question 103
A company relies on an ICS to perform equipment monitoring functions that are federally mandated for operation of the facility. Fines for non-compliance could be costly. The ICS has known vulnerabilities and can no longer be patched or updated. Cyber-liability insurance cannot be obtained because insurance companies will not insure this equipment.
Which of the following would be the BEST option to manage this risk to the company's production environment?
Which of the following would be the BEST option to manage this risk to the company's production environment?
Question 104
Immediately following the report of a potential breach, a security engineer creates a forensic image of the server in question as part of the organization incident response procedure. Which of the must occur to ensure the integrity of the image?
Question 105
Security policies that are in place at an organization prohibit USB drives from being utilized across the entire enterprise, with adequate technical controls in place to block them. As a way to still be able to work from various locations on different computing resources, several sales staff members have signed up for a web-based storage solution without the consent of the IT department. However, the operations department is required to use the same service to transmit certain business partner documents.
Which of the following would BEST allow the IT department to monitor and control this behavior?
Which of the following would BEST allow the IT department to monitor and control this behavior?