Question 201
A product manager is concerned about the unintentional sharing of the company's intellectual property through employees' use of social media. Which of the following would BEST mitigate this risk?
Question 202
A security analyst is trying to identify the source of a recent data loss incident. The analyst has reviewed all the for the time surrounding the identified all the assets on the network at the time of the data loss. The analyst suspects the key to finding the source was obfuscated in an application. Which of the following tools should the analyst use NEXT?
Question 203
A laptop is recovered a few days after it was stolen.
Which of the following should be verified during incident response activities to determine the possible impact of the incident?
Which of the following should be verified during incident response activities to determine the possible impact of the incident?
Question 204
Using SSL, an administrator wishes to secure public facing server farms in three subdomains:
dc1.east.company.com, dc2.central.company.com, and dc3.west.company.com. Which of the following is the number of wildcard SSL certificates that should be purchased?
dc1.east.company.com, dc2.central.company.com, and dc3.west.company.com. Which of the following is the number of wildcard SSL certificates that should be purchased?
Question 205
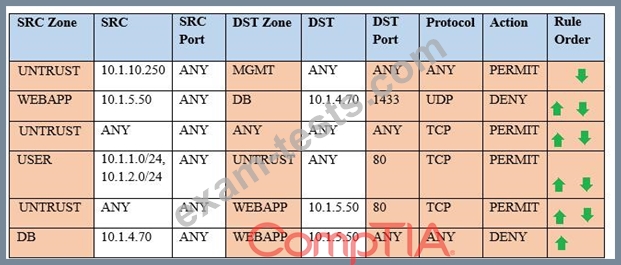
Compliance with company policy requires a quarterly review of firewall rules.
You are asked to conduct a review on the internal firewall sitting between several internal networks.
The intent of this firewall is to make traffic more secure.
Given the following information perform the tasks listed below:
Untrusted zone: 0.0.0.0/0
User zone: USR 10.1.1.0/24
User zone: USR2 10.1.2.0/24
DB zone: 10.1.0/24
Web application zone: 10.1.5.0/24
Management zone: 10.1.10.0/24
Web server: 10.1.5.50
MS-SQL server: 10.1.4.70
MGMT platform: 10.1.10.250
Task 1) A rule was added to prevent the management platform from accessing the internet. This rule is not working. Identify the rule and correct this issue.
Task 2) The firewall must be configured so that the SQL server can only receive requests from the web server.
Task 3) The web server must be able to receive unencrypted requests from hosts inside and outside the corporate network.
Task 4) Ensure the final rule is an explicit deny.
Task 5) Currently the user zone can access internet websites over an unencrypted protocol. Modify a rule so that user access to websites is over secure protocols only.
Instructions: To perform the necessary tasks, please modify the DST port, SRC zone, Protocol, Action, and/or Rule Order columns. Type ANY to include all ports. Firewall ACLs are read from the top down. Once you have met the simulation requirements, click Save. When you have completed the simulation, please select the Done button to submit.
Once the simulation is submitted, please select the Next button to continue.

