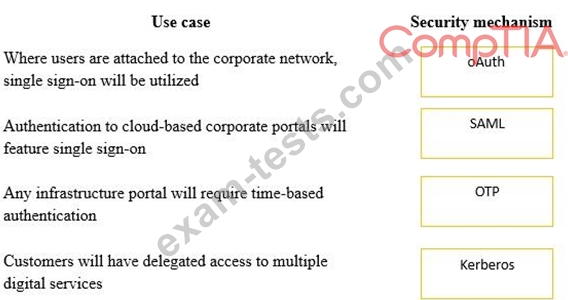
Question 186
A security consultant is considering authentication options for a financial institution. The following authentication options are available. Drag and drop the security mechanism to the appropriate use case.
Options may be used once.

Options may be used once.

Question 187
A bank is in the process of developing a new mobile application. The mobile client renders content and communicates back to the company servers via REST/JSON calls. The bank wants to ensure that the communication is stateless between the mobile application and the web services gateway. Which of the following controls MUST be implemented to enable stateless communication?
Question 188
An asset manager is struggling with the best way to reduce the time required to perform asset location activities in a large warehouse.
A project manager indicated that RFID might be a valid solution if the asset manager's requirements were supported by current RFID capabilities.
Which of the following requirements would be MOST difficult for the asset manager to implement?
A project manager indicated that RFID might be a valid solution if the asset manager's requirements were supported by current RFID capabilities.
Which of the following requirements would be MOST difficult for the asset manager to implement?
Question 189
A company monitors the performance of all web servers using WMI. A network administrator informs the security engineer that web servers hosting the company's client- facing portal are running slowly today. After some investigation, the security engineer notices a large number of attempts at enumerating host information via SNMP from multiple IP addresses. Which of the following would be the BEST technique for the security engineer to employ in an attempt to prevent reconnaissance activity?
Question 190
A security team wants to keep up with emerging threats more efficiently by automating NIDS signature development and deployment Which of the following approaches, would BEST support this objective?