Question 6
After an employee was terminated, the company discovered the employee still had access to emails and attached content that should have been destroyed during the off-boarding. The employee's laptop and cell phone were confiscated and accounts were disabled promptly. Forensic investigation suggests the company's DLP was effective, and the content in question was not sent outside of work or transferred to removable media.
Personality owned devices are not permitted to access company systems or information.
Which of the following would be the MOST efficient control to prevent this from occurring in the future?
Personality owned devices are not permitted to access company systems or information.
Which of the following would be the MOST efficient control to prevent this from occurring in the future?
Question 7
A security incident responder discovers an attacker has gained access to a network and has overwritten key system files with backdoor software. The server was reimaged and patched offline.
Which of the following tools should be implemented to detect similar attacks?
Which of the following tools should be implemented to detect similar attacks?
Question 8
A threat advisory alert was just emailed to the IT security staff. The alert references specific types of host operating systems that can allow an unauthorized person to access files on a system remotely. A fix was recently published, but it requires a recent endpoint protection engine to be installed prior to running the fix.
Which of the following MOST likely need to be configured to ensure the system are mitigated accordingly?
(Choose two.)
Which of the following MOST likely need to be configured to ensure the system are mitigated accordingly?
(Choose two.)
Question 9
Providers at a healthcare system with many geographically dispersed clinics have been fined five times this year after an auditor received notice of the following SMS messages:
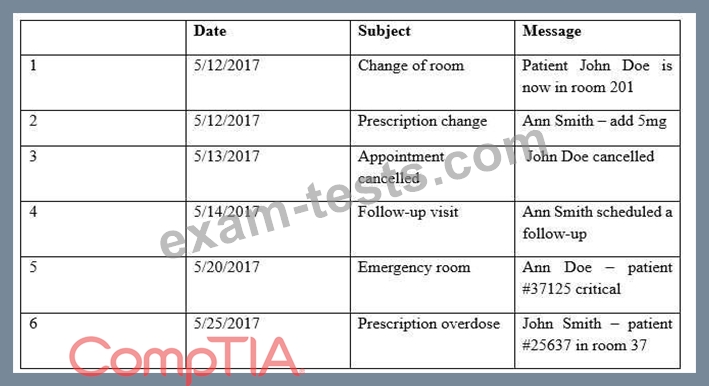
Which of the following represents the BEST solution for preventing future fines?

Which of the following represents the BEST solution for preventing future fines?
Question 10
A technician is validating compliance with organizational policies. The user and machine accounts in the AD are not set to expire, which is non-compliant. Which of the following network tools would provide this type of information?

