Question 531
A security researcher at an organization is reviewing potential threats to the VolP phone system infrastructure which uses a gigabit Internet connection. The researcher finds a vulnerability and knows placing an IPS in front of the phone system will mitigate the risk. The researcher gathers the following information about various IPS systems:
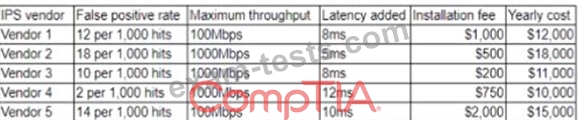
The organization is concerned about cost, but call quality is critical to its operations Which of the foAotmng vendors would be BEST for the organization to choose?

The organization is concerned about cost, but call quality is critical to its operations Which of the foAotmng vendors would be BEST for the organization to choose?
Question 532
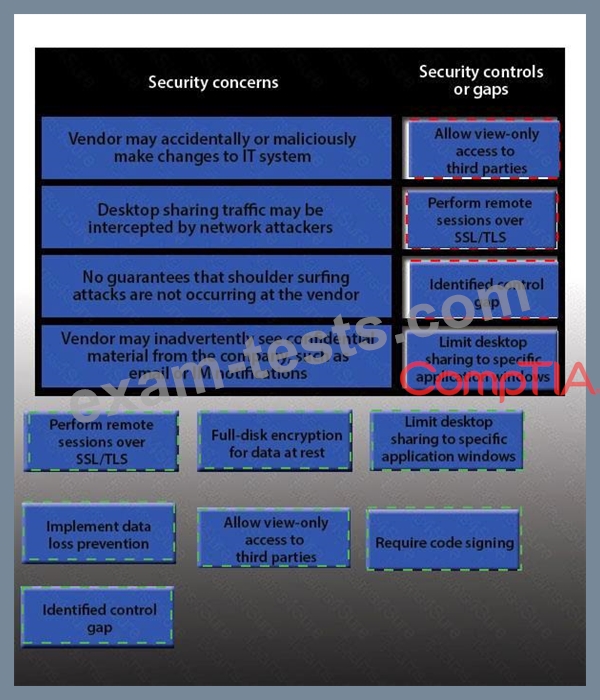
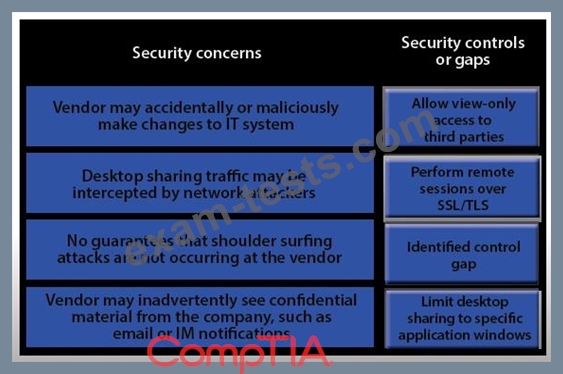
IT staff within a company often conduct remote desktop sharing sessions with vendors to troubleshoot vendor product-related issues. Drag and drop the following security controls to match the associated security concern.
Options may be used once or not at all.
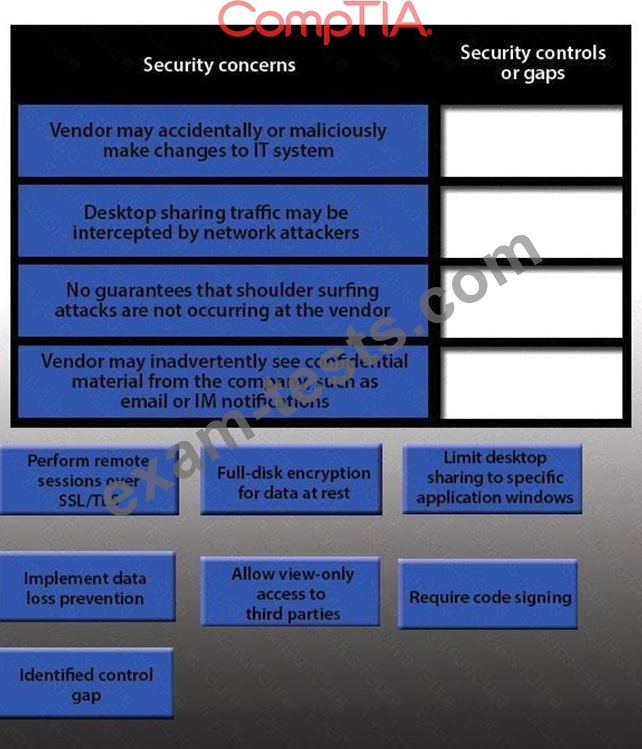
Options may be used once or not at all.

Question 533
A system engineer is reviewing output from a web application vulnerability scan. The engineer has determined data is entering the application from an untrusted source and is being used to construct a query dynamically. Which of the following code snippets would BEST protect the application against an SQL injection attack?
A)
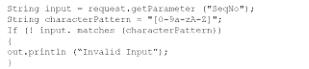
B)

C)
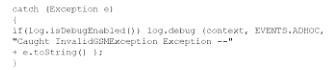
D)
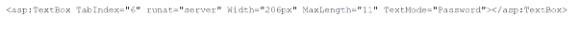
A)

B)

C)

D)
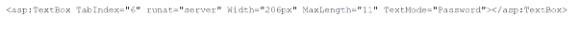
Question 534
A recent CRM upgrade at a branch office was completed after the desired deadline. Several technical issues were found during the upgrade and need to be discussed in depth before the next branch office is upgraded.
Which of the following should be used to identify weak processes and other vulnerabilities?
Which of the following should be used to identify weak processes and other vulnerabilities?
Question 535
A security administrator wants to allow external organizations to cryptographically validate the company's domain name in email messages sent by employees. Which of the following should the security administrator implement?