Question 71
A security architect for a large, multinational manufacturer needs to design and implement a security solution to monitor traffic.
When designing the solution, which of the following threats should the security architect focus on to prevent attacks against the OT network?
When designing the solution, which of the following threats should the security architect focus on to prevent attacks against the OT network?
Question 72
A software house is developing a new application. The application has the following requirements:
Reduce the number of credential requests as much as possible
Integrate with social networks
Authenticate users
Which of the following is the BEST federation method to use for the application?
Reduce the number of credential requests as much as possible
Integrate with social networks
Authenticate users
Which of the following is the BEST federation method to use for the application?
Question 73
A company security engineer arrives at work to face the following scenario:
1) Website defacement
2) Calls from the company president indicating the website needs to be fixed Immediately because It Is damaging the brand
3) A Job offer from the company's competitor
4) A security analyst's investigative report, based on logs from the past six months, describing how lateral movement across the network from various IP addresses originating from a foreign adversary country resulted in exfiltrated data Which of the following threat actors Is MOST likely involved?
1) Website defacement
2) Calls from the company president indicating the website needs to be fixed Immediately because It Is damaging the brand
3) A Job offer from the company's competitor
4) A security analyst's investigative report, based on logs from the past six months, describing how lateral movement across the network from various IP addresses originating from a foreign adversary country resulted in exfiltrated data Which of the following threat actors Is MOST likely involved?
Question 74
A company wants to improve Its active protection capabilities against unknown and zero-day malware. Which of the following Is the MOST secure solution?
Question 75
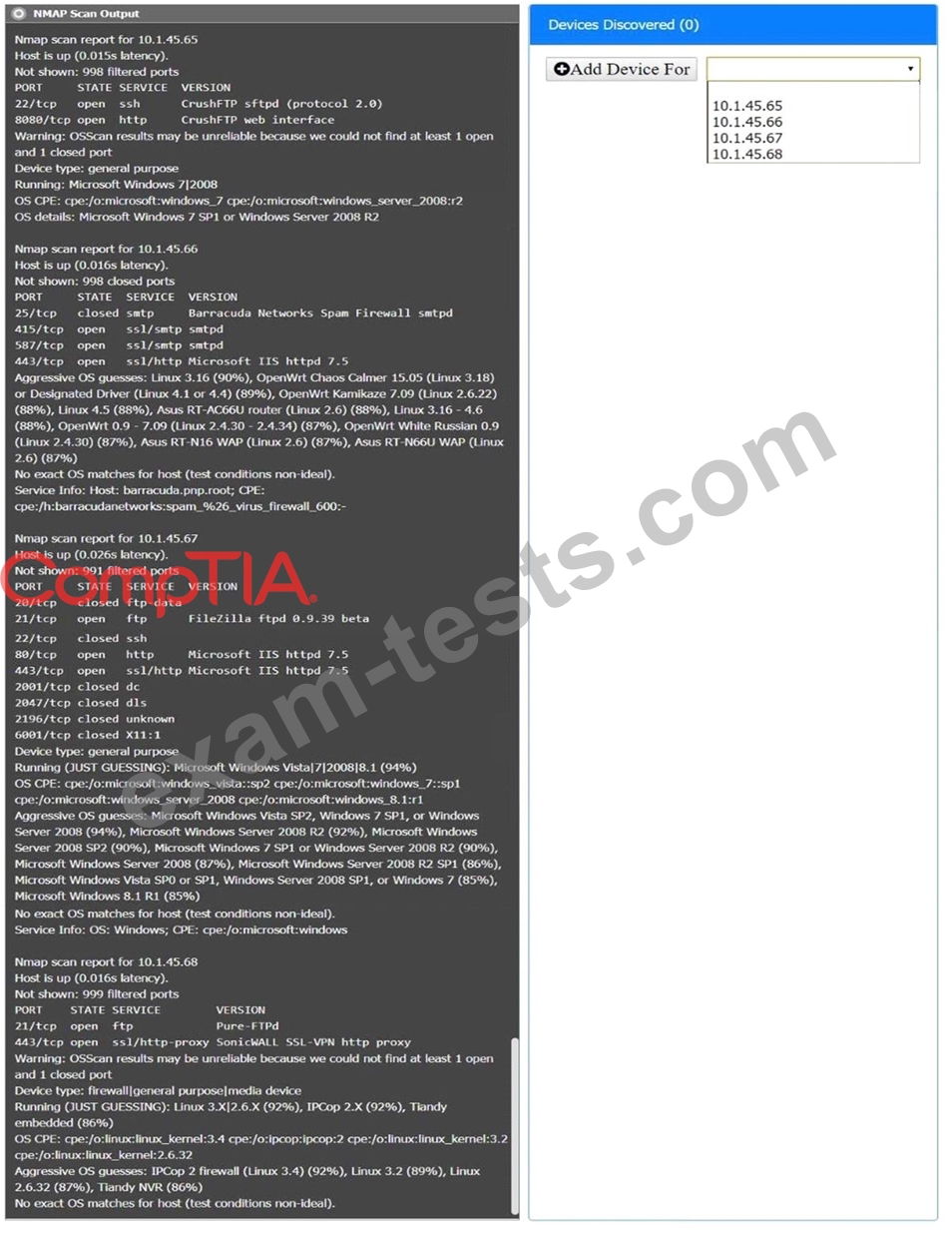
SIMULATION
You are a security analyst tasked with interpreting an Nmap scan output from company's privileged network.
The company's hardening guidelines indicate the following:
There should be one primary server or service per device.
Only default ports should be used.
Non-secure protocols should be disabled.
INSTRUCTIONS
Using the Nmap output, identify the devices on the network and their roles, and any open ports that should be closed.
For each device found by Nmap, add a device entry to the Devices Discovered list, with the following information:
The IP address of the device
The primary server or service of the device (Note that each IP should by associated with one service/port only) The protocol(s) that should be disabled based on the hardening guidelines (Note that multiple ports may need to be closed to comply with the hardening guidelines) If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
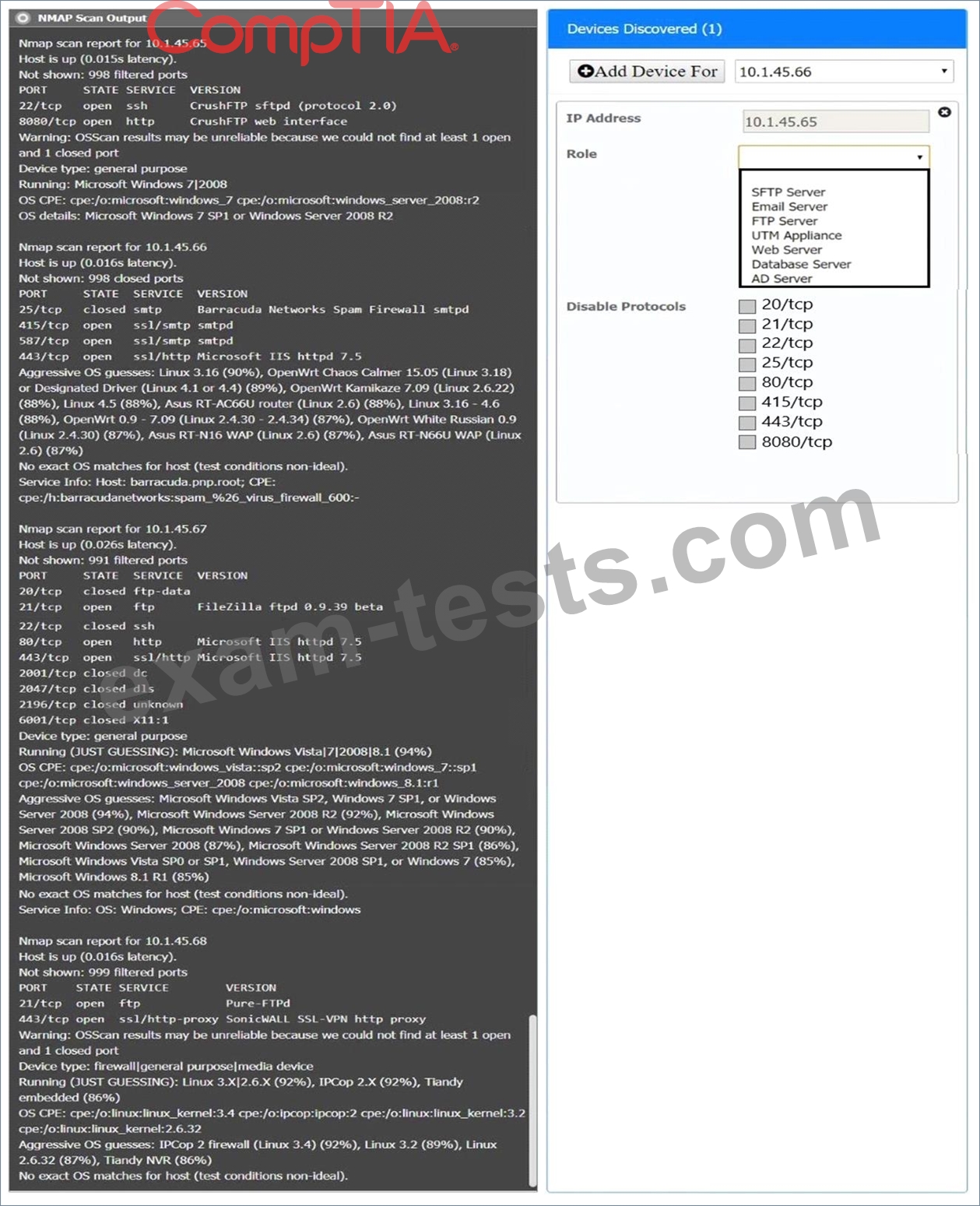
You are a security analyst tasked with interpreting an Nmap scan output from company's privileged network.
The company's hardening guidelines indicate the following:
There should be one primary server or service per device.
Only default ports should be used.
Non-secure protocols should be disabled.
INSTRUCTIONS
Using the Nmap output, identify the devices on the network and their roles, and any open ports that should be closed.
For each device found by Nmap, add a device entry to the Devices Discovered list, with the following information:
The IP address of the device
The primary server or service of the device (Note that each IP should by associated with one service/port only) The protocol(s) that should be disabled based on the hardening guidelines (Note that multiple ports may need to be closed to comply with the hardening guidelines) If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.


Premium Bundle
Newest CAS-004 Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing CAS-004 Exam! BraindumpsPass.com now offer the updated CAS-004 exam dumps, the BraindumpsPass.com CAS-004 exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com CAS-004 pdf dumps with Exam Engine here:

