Question 61
A company's Chief Information Security Officer is concerned that the company's proposed move to the cloud could lead to a lack of visibility into network traffic flow logs within the VPC.
Which of the following compensating controls would be BEST to implement in this situation?
Which of the following compensating controls would be BEST to implement in this situation?
Question 62
A threat analyst notices the following URL while going through the HTTP logs.

Which of the following attack types is the threat analyst seeing?

Which of the following attack types is the threat analyst seeing?
Question 63
A company wants to quantify and communicate the effectiveness of its security controls but must establish measures. Which of the following is MOST likely to be included in an effective assessment roadmap for these controls?
Question 64
A cybersecurity engineer analyst a system for vulnerabilities. The tool created an OVAL. Results document as output. Which of the following would enable the engineer to interpret the results in a human readable form? (Select TWO.)
Question 65
A large number of emails have been reported, and a security analyst is reviewing the following information from the emails:
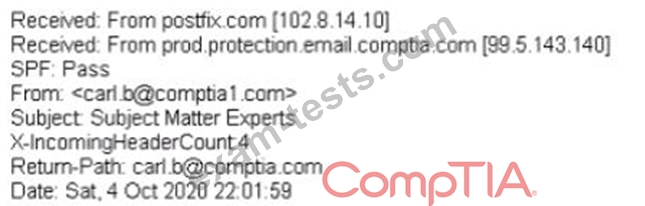
As part of the image process, which of the following is the FIRST step the analyst should take?

As part of the image process, which of the following is the FIRST step the analyst should take?
Premium Bundle
Newest CAS-004 Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing CAS-004 Exam! BraindumpsPass.com now offer the updated CAS-004 exam dumps, the BraindumpsPass.com CAS-004 exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com CAS-004 pdf dumps with Exam Engine here:

