Question 46
A company has a 40Gbps network that uses a network tap to inspect the traffic using an IDS. The IDS usually performs normally except when the servers are downloading patches from their local update repository
10.10.10.139 using HTTPS. During the patch windows, the IDS cannot handle the extra load and drops a significant number of packets. Which of the following would allow a network engineer to prevent this issue without compromising the network visibility?
10.10.10.139 using HTTPS. During the patch windows, the IDS cannot handle the extra load and drops a significant number of packets. Which of the following would allow a network engineer to prevent this issue without compromising the network visibility?
Question 47
An organization's Chief Technical Officer is concerned that changes to the network using IaC are causing unscheduled outages. Which of the following best mitigates this risk?
Question 48
A network architect must ensure only certain departments can access specific resources while on premises.
Those same users cannot be allowed to access those resources once they have left campus. Which of the following would ensure access is provided according to these requirements?
Those same users cannot be allowed to access those resources once they have left campus. Which of the following would ensure access is provided according to these requirements?
Question 49
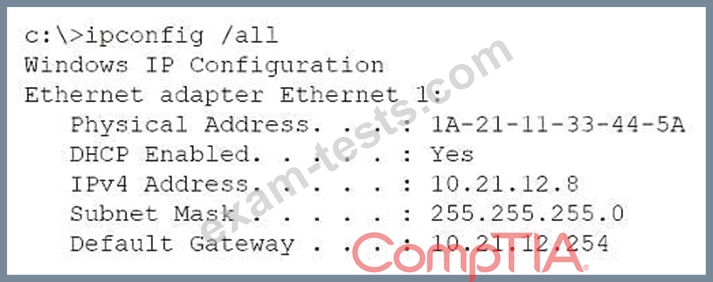
A network administrator is troubleshooting a user's workstation that is unable to connect to the company network. The results of ipconfig and arp -a are shown. The user's workstation:
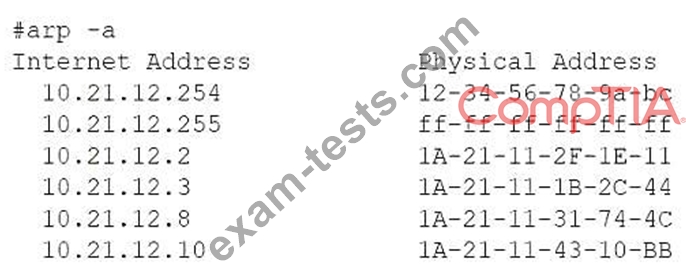
A router on the same network shows the following output:
* Has an IP address of 10.21.12.8
* Has subnet mask 255.255.255.0
* Default gateway is 10.21.12.254
* ARP table shows 10.21.12.8 mapped to 1A-21-11-31-74-4C (a different MAC address than the local adapter)

A router on the same network shows the following output:

* Has an IP address of 10.21.12.8
* Has subnet mask 255.255.255.0
* Default gateway is 10.21.12.254
* ARP table shows 10.21.12.8 mapped to 1A-21-11-31-74-4C (a different MAC address than the local adapter)
Question 50
A network security engineer must secure a web application running on virtual machines in a public cloud. The virtual machines are behind an application load balancer. Which of the following technologies should the engineer use to secure the virtual machines? (Choose two.)

