Question 121
Due to new regulations, a company has decided to institute an organizational vulnerability management program and assign the function to the security team.
Which of the following frameworks would BEST support the program? (Select two.)
Which of the following frameworks would BEST support the program? (Select two.)
Question 122
After a breach involving the exfiltration of a large amount of sensitive data a security analyst is reviewing the following firewall logs to determine how the breach occurred:
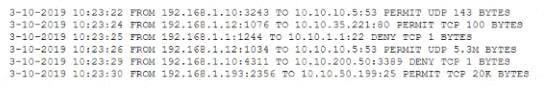
Which of the following IP addresses does the analyst need to investigate further?

Which of the following IP addresses does the analyst need to investigate further?
Question 123
A malicious hacker wants to gather guest credentials on a hotel 802.11 network. Which of the following tools is the malicious hacker going to use to gain access to information found on the hotel network?
Question 124
A cybersecurity professional typed in a URL and discovered the admin panel for the e-commerce application is accessible over the open web with the default password.
Which of the following is the MOST secure solution to remediate this vulnerability?
Which of the following is the MOST secure solution to remediate this vulnerability?
Question 125
A security analyst is investigating a compromised Linux server.
The analyst issues the ps command and receives the following output.
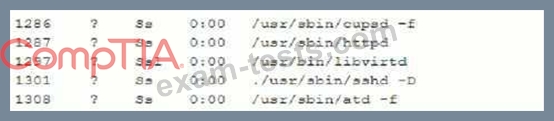
Which of the following commands should the administrator run NEXT to further analyze the compromised system?
The analyst issues the ps command and receives the following output.

Which of the following commands should the administrator run NEXT to further analyze the compromised system?
Premium Bundle
Newest CS0-002 Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing CS0-002 Exam! BraindumpsPass.com now offer the updated CS0-002 exam dumps, the BraindumpsPass.com CS0-002 exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com CS0-002 pdf dumps with Exam Engine here:

