Question 101
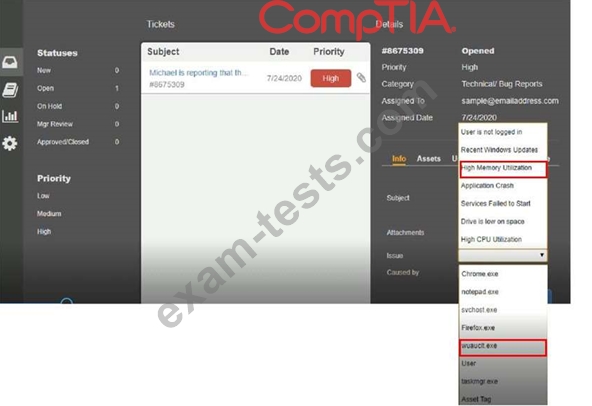
A security analyst, who is working for a company that utilizes Linux servers, receives the following results from a vulnerability scan:
Which of the following is MOST likely a false positive?

Which of the following is MOST likely a false positive?
Question 102
A security analyst is evaluating two vulnerability management tools for possible use in an organization. The analyst set up each of the tools according to the respective vendor's instructions and generated a report of vulnerabilities that ran against the same target server.
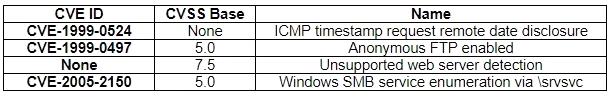
Tool A reported the following:
Tool B reported the following:

Which of the following BEST describes the method used by each tool? (Choose two.)
Tool A reported the following:

Tool B reported the following:

Which of the following BEST describes the method used by each tool? (Choose two.)
Question 103
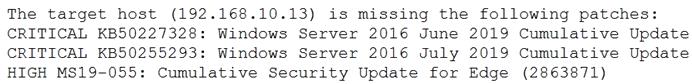
Welcome to the Enterprise Help Desk System. Please work the ticket escalated to you in the desk ticket queue.
INSTRUCTIONS
Click on me ticket to see the ticket details Additional content is available on tabs within the ticket First, select the appropriate issue from the drop-down menu. Then, select the MOST likely root cause from second drop-down menu If at any time you would like to bring back the initial state of the simulation, please click the Reset All button
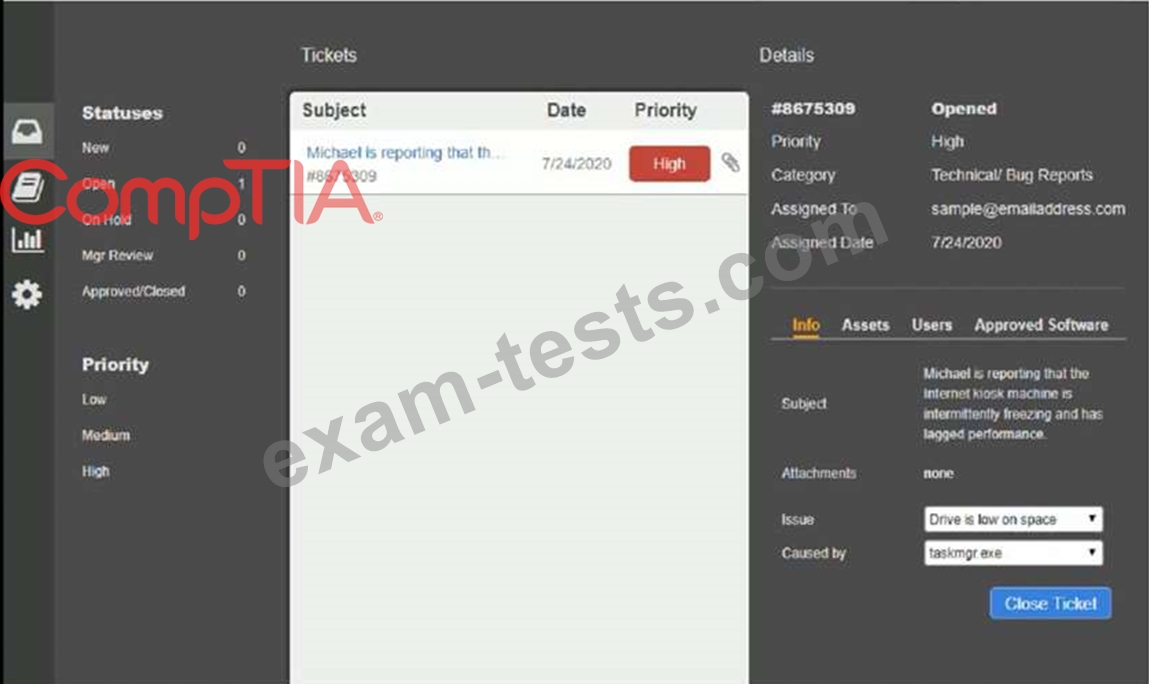
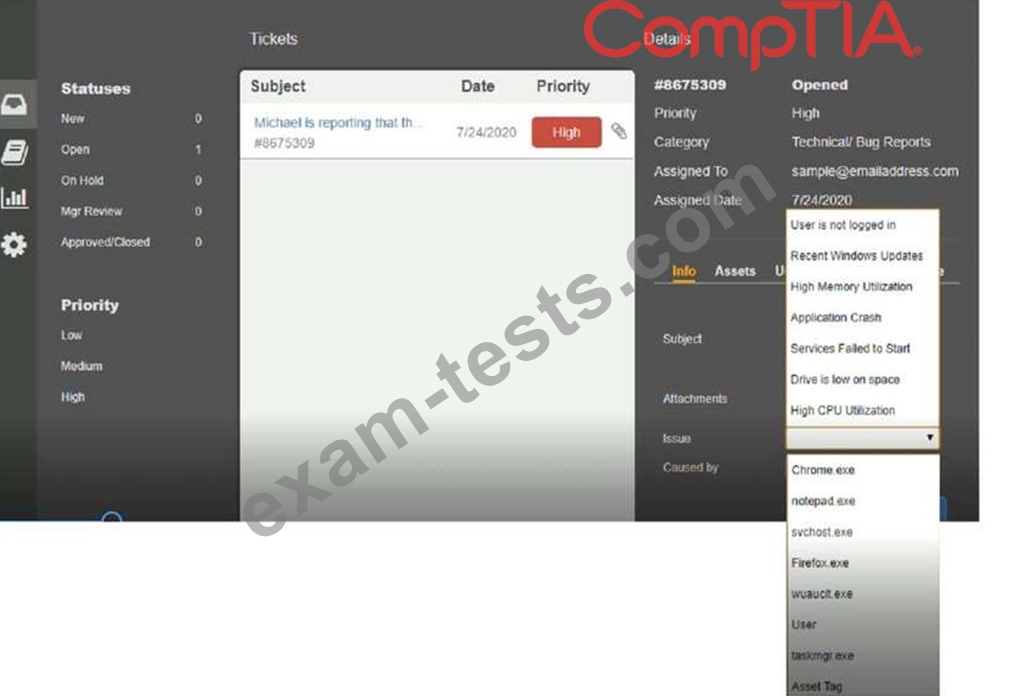
INSTRUCTIONS
Click on me ticket to see the ticket details Additional content is available on tabs within the ticket First, select the appropriate issue from the drop-down menu. Then, select the MOST likely root cause from second drop-down menu If at any time you would like to bring back the initial state of the simulation, please click the Reset All button


Question 104
An executive assistant wants to onboard a new cloud based product to help with business analytics and dashboarding. When of the following would be the BEST integration option for the service?
Question 105
Joe, a user, is unable to launch an application on his laptop, which he typically uses on a daily basis. Joe informs a security analyst of the issue. After an online database comparison, the security analyst checks the SIEM and notices alerts indicating certain .txt and .dll files are blocked. Which of the following tools would generate these logs?
Premium Bundle
Newest CS0-002 Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing CS0-002 Exam! BraindumpsPass.com now offer the updated CS0-002 exam dumps, the BraindumpsPass.com CS0-002 exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com CS0-002 pdf dumps with Exam Engine here: