Question 11
A security analyst conducted a risk assessment on an organization's wireless network and identified a high-risk element in the implementation of data confidentially protection. Which of the following is the BEST technical security control to mitigate this risk?
Question 12
A cybersecurity analyst is currently using Nessus to scan several FTP servers. Upon receiving the results of the scan, the analyst needs to further test to verify that the vulnerability found exists.
The analyst uses the following snippet of code:
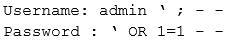
Which of the following vulnerabilities is the analyst checking for?
The analyst uses the following snippet of code:

Which of the following vulnerabilities is the analyst checking for?
Question 13
An information security analyst observes anomalous behavior on the SCADA devices in a power plant. This behavior results in the industrial generators overheating and destabilizing the power supply.
Which of the following would BEST identify potential indicators of compromise?
Which of the following would BEST identify potential indicators of compromise?
Question 14
A cybersecurity analyst was asked to review several results of web vulnerability scan logs.
Given the following snippet of code:
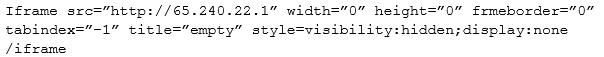
Which of the following BEST describes the situation and recommendations to be made?
Given the following snippet of code:
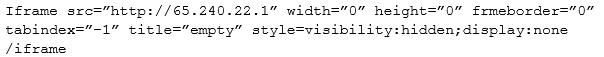
Which of the following BEST describes the situation and recommendations to be made?
Question 15
A security analyst is reviewing the following log entries to identify anomalous activity:
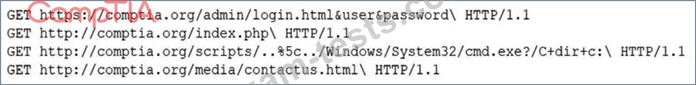
Which of the following attack types is occurring?

Which of the following attack types is occurring?

