Question 36
A cybersecurity analyst is currently auditing a new Active Directory server for compliance. The analyst uses Nessus to do the initial scan, and Nessus reports the following:
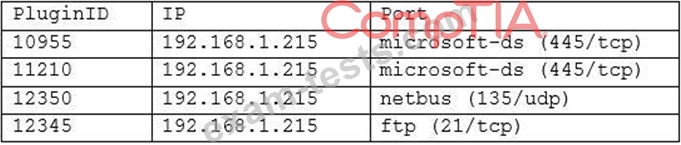
Which of the following critical vulnerabilities has the analyst discovered?

Which of the following critical vulnerabilities has the analyst discovered?
Question 37
An organization recently discovered some inconsistencies in the motherboards it received from a vendor. The organization's security team then provided guidance on how to ensure the authenticity of the motherboards it received from vendors.
Which of the following would be the BEST recommendation for the security analyst to provide'?
Which of the following would be the BEST recommendation for the security analyst to provide'?
Question 38
When reviewing the system logs, the cybersecurity analyst noticed a suspicious log entry:
wmic /node: HRDepartment1 computersystem get username
Which of the following combinations describes what occurred, and what action should be taken in this situation?
wmic /node: HRDepartment1 computersystem get username
Which of the following combinations describes what occurred, and what action should be taken in this situation?
Question 39
A cybersecurity analyst has received a report that multiple systems are experiencing slowness as a result of a DDoS attack.
Which of the following would be the BEST action for the cybersecurity analyst to perform?
Which of the following would be the BEST action for the cybersecurity analyst to perform?
Question 40
A security analyst reviews the following aggregated output from an Nmap scan and the border firewall ACL:
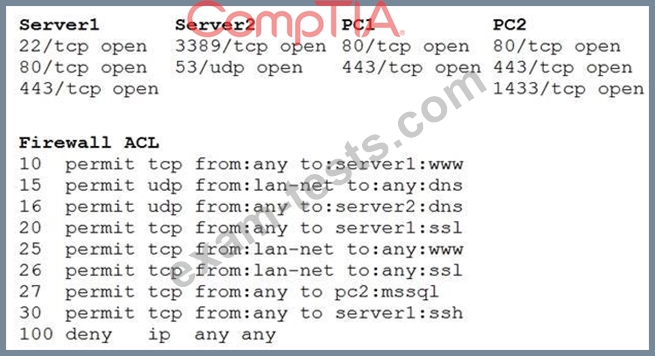
Which of the following should the analyst reconfigure to BEST reduce organizational risk while maintaining current functionality?

Which of the following should the analyst reconfigure to BEST reduce organizational risk while maintaining current functionality?

