Question 106
A financial organization has offices located globally. Per the organization's policies and procedures, all executives who conduct Business overseas must have their mobile devices checked for malicious software or evidence of tempering upon their return. The information security department oversees the process, and no executive has had a device compromised. The Chief information Security Officer wants to Implement an additional safeguard to protect the organization's dat
a. Which of the following controls would work BEST to protect the privacy of the data if a device is stolen?
a. Which of the following controls would work BEST to protect the privacy of the data if a device is stolen?
Question 107
A security is reviewing a vulnerability scan report and notes the following finding:
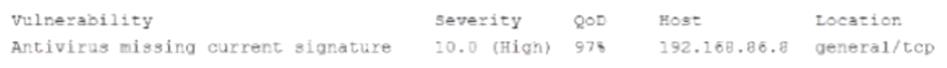
As part of the detection and analysis procedures, which of the following should the analyst do NEXT?

As part of the detection and analysis procedures, which of the following should the analyst do NEXT?
Question 108
An organization is developing software to match customers' expectations. Before the software goes into production, it must meet the following quality assurance guidelines
* Uncover all the software vulnerabilities.
* Safeguard the interest of the software's end users.
* Reduce the likelihood that a defective program will enter production.
* Preserve the Interests of me software producer
Which of me following should be performed FIRST?
* Uncover all the software vulnerabilities.
* Safeguard the interest of the software's end users.
* Reduce the likelihood that a defective program will enter production.
* Preserve the Interests of me software producer
Which of me following should be performed FIRST?
Question 109
A security analyst conducted a risk assessment on an organization's wireless network and identified a high-risk element in the implementation of data confidentially protection. Which of the following is the BEST technical security control to mitigate this risk?
Question 110
While investigating an incident in a company's SIEM console, a security analyst found hundreds of failed SSH login attempts, which all occurred in rapid succession. The failed attempts were followed by a successful login on the root user Company policy allows systems administrators to manage their systems only from the company's internal network using their assigned corporate logins. Which of the following are the BEST actions the analyst can take to stop any further compromise? (Select TWO).

