Question 101
A newly appointed Chief Information Security Officer (CISO) has completed a risk assessment review of the organization and wants to reduce the numerous risks that were identified. Which of the following will provide a trend of risk mitigation?
Question 102
Following a recent security breach, a company decides to investigate account usage to ensure privileged accounts are only being utilized during typical business hours. During the investigation, a security analyst determines an account was consistently utilized in the middle of the night.
Which of the following actions should the analyst take NEXT?
Which of the following actions should the analyst take NEXT?
Question 103
An analyst is reviewing the following code output of a vulnerability scan:
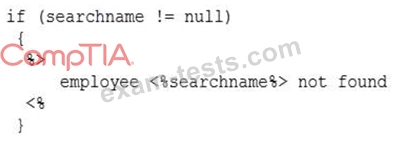
Which of the following types of vulnerabilities does this MOST likely represent?

Which of the following types of vulnerabilities does this MOST likely represent?
Question 104
A security analyst is researching ways to improve the security of a company's email system to mitigate emails that are impersonating company executives. Which of the following would be BEST for the analyst to configure to achieve this objective?
Question 105
An analyst has received a notification about potential malicious activity against a web server. The analyst logs in to a central log collection server and runs the following command: "cat access.log.1 | grep "union". The output shown below appears:
<68.71.54.117> - - [31/Jan/2020:10:02:31 -0400] "Get /cgi-bin/backend1.sh?id=%20union%20select%20192.168.60.50 HTTP/1.1"
Which of the following attacks has occurred on the server?
<68.71.54.117> - - [31/Jan/2020:10:02:31 -0400] "Get /cgi-bin/backend1.sh?id=%20union%20select%20192.168.60.50 HTTP/1.1"
Which of the following attacks has occurred on the server?

