Question 131
A large software company wants to move As source control and deployment pipelines into a cloud-computing environment. Due to the nature of the business management determines the recovery time objective needs to be within one hour. Which of the following strategies would put the company in the BEST position to achieve the desired recovery time?
Question 132
A monthly job to install approved vendor software updates and hot fixes recently stopped working. The security team performed a vulnerability scan, which identified several hosts as having some critical OS vulnerabilities, as referenced in the common vulnerabilities and exposures (CVE) database.
Which of the following should the security team do NEXT to resolve the critical findings in the most effective manner? (Choose two.)
Which of the following should the security team do NEXT to resolve the critical findings in the most effective manner? (Choose two.)
Question 133
A security analyst reviews SIEM logs and discovers the following error event:

Which of the following environments does the analyst need to examine to continue troubleshooting the event?

Which of the following environments does the analyst need to examine to continue troubleshooting the event?
Question 134
An organization was alerted to a possible compromise after its proprietary data was found for sale on the Internet. An analyst is reviewing the logs from the next-generation UTM in an attempt to find evidence of this breach. Given the following output:
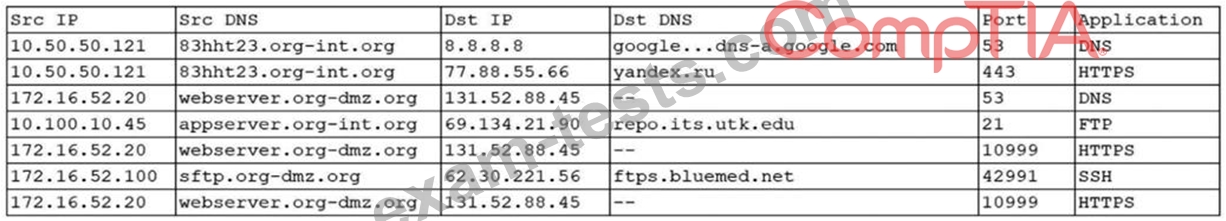
Which of the following should be the focus of the investigation?

Which of the following should be the focus of the investigation?
Question 135
Which of the following BEST articulates the benefit of leveraging SCAP in an organization's cybersecurity analysis toolset?
Premium Bundle
Newest CS0-002 Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing CS0-002 Exam! BraindumpsPass.com now offer the updated CS0-002 exam dumps, the BraindumpsPass.com CS0-002 exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com CS0-002 pdf dumps with Exam Engine here:

