Question 1
A security analyst obtained the following table of results from a recent vulnerability assessment that was conducted against a single web server in the environment:
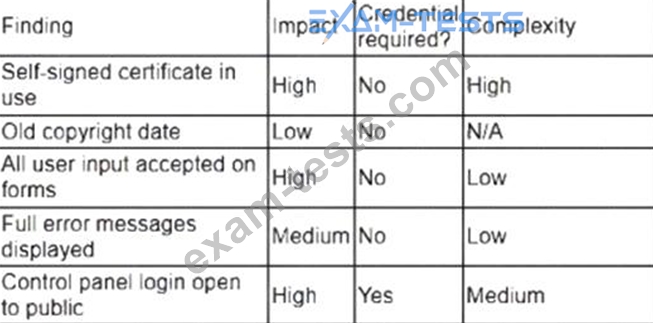
Which of the following should be completed first to remediate the findings?

Which of the following should be completed first to remediate the findings?
Question 2
The security team at a company, which was a recent target of ransomware, compiled a list of hosts that were identified as impacted and in scope for this incident. Based on the following host list:
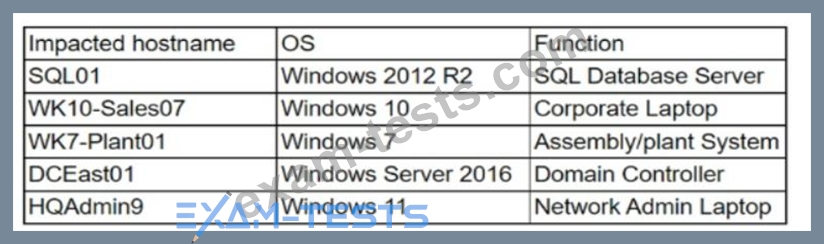
Which of the following systems was most pivotal to the threat actor in its distribution of the encryption binary via Group Policy?

Which of the following systems was most pivotal to the threat actor in its distribution of the encryption binary via Group Policy?
Question 3
A vulnerability scan of a web server that is exposed to the internet was recently completed. A security analyst is reviewing the resulting vector strings:
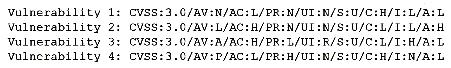
Which of the following vulnerabilities should be patched first?

Which of the following vulnerabilities should be patched first?
Question 4
A security analyst discovers an LFI vulnerability that can be exploited to extract credentials from the underlying host. Which of the following patterns can the security analyst use to search the web server logs for evidence of exploitation of that particular vulnerability?
Question 5
A systems administrator receives reports of an internet-accessible Linux server that is running very sluggishly.
The administrator examines the server, sees a high amount of memory utilization, and suspects a DoS attack related to half-open TCP sessions consuming memory. Which of the following tools would best help to prove whether this server was experiencing this behavior?
The administrator examines the server, sees a high amount of memory utilization, and suspects a DoS attack related to half-open TCP sessions consuming memory. Which of the following tools would best help to prove whether this server was experiencing this behavior?

