Question 36
During an incident, some loCs of possible ransomware contamination were found in a group of servers in a segment of the network. Which of the following steps should be taken next?
Question 37
A security analyst is trying to validate the results of a web application scan with Burp Suite. The security analyst performs the following:
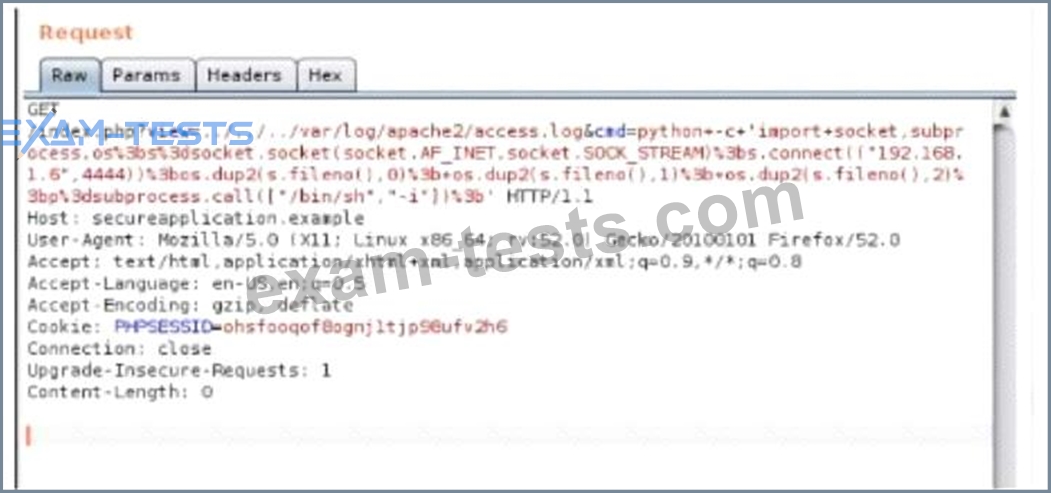
Which of the following vulnerabilitles Is the securlty analyst trylng to valldate?

Which of the following vulnerabilitles Is the securlty analyst trylng to valldate?
Question 38
A security team conducts a lessons-learned meeting after struggling to determine who should conduct the next steps following a security event. Which of the following should the team create to address this issue?
Question 39
When investigating a potentially compromised host, an analyst observes that the process BGInfo.exe (PID 1024), a Sysinternals tool used to create desktop backgrounds containing host details, has been running for over two days. Which of the following activities will provide the best insight into this potentially malicious process, based on the anomalous behavior?
Question 40
Following a recent security incident, the Chief Information Security Officer is concerned with improving visibility and reporting of malicious actors in the environment. The goal is to reduce the time to prevent lateral movement and potential data exfiltration. Which of the following techniques will best achieve the improvement?

