Question 16
In an FC SAN environment, an administrator wants to ensure that a particular switch port cannot function as an E_Port and cannot be used to create an interswitch link. Which security mechanism should the administrator use?
Question 17
A system has three components and all three components need to be operational for 24 hours; Monday through Friday. During a particular week, failure of component 1 occurred as follows:
-Tuesday = 8 AM to 11 AM -Thursday = 8 PM to 10 PM -Friday = 5 AM to 9 AM What is the mean time between failures on component 1 for that week?
-Tuesday = 8 AM to 11 AM -Thursday = 8 PM to 10 PM -Friday = 5 AM to 9 AM What is the mean time between failures on component 1 for that week?
Question 18
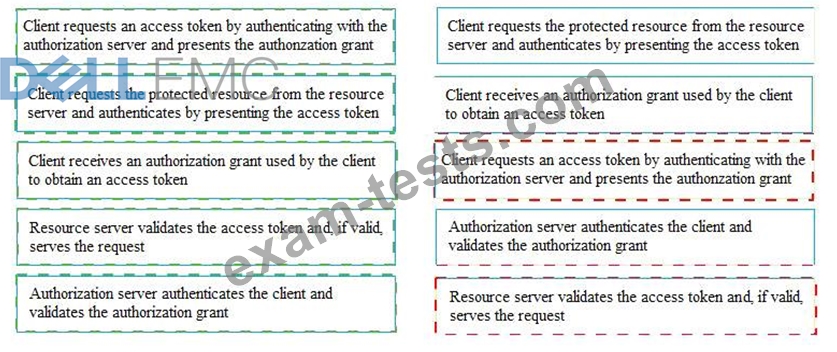
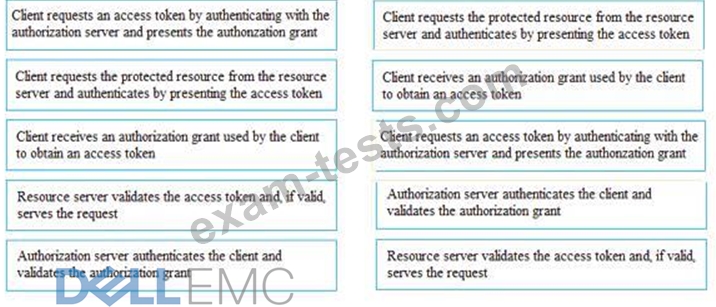
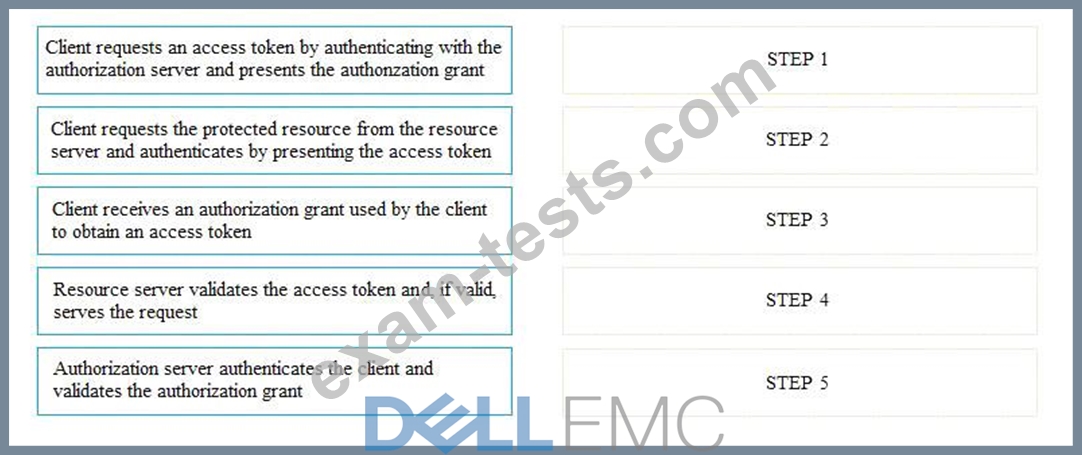
If the client requests authorization from the resource owner, what are the remaining sequence of steps to authenticate a user using OAuth control?

Question 19
A company wants to implement a Fibre Channel (FC) SAN topology. The implementation will involve deploying four switches for localized compute and storage system connectivity. In addition, to meet their applications' performance requirements, they need a maximum of one ISL and redundant connections for their compute to storage traffic.
Which topology should be recommended?
Which topology should be recommended?
Question 20
What is an accurate statement about hypervisor-based continuous data protection (CDP)?