Question 26
What is an advantage of implementing file-level virtualization in a data center environment?
Question 27
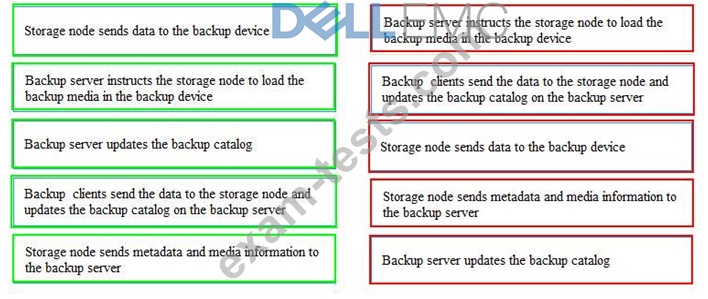
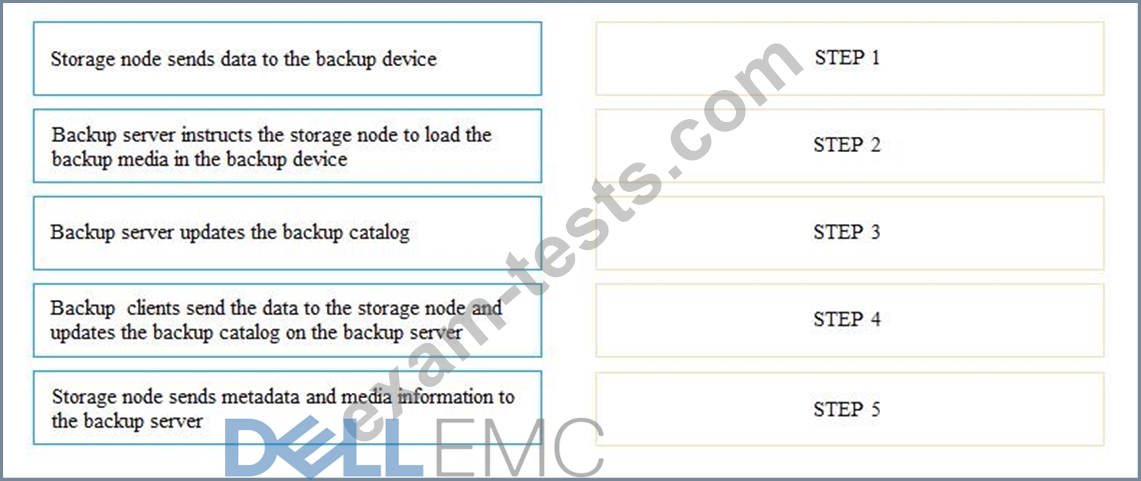
In a backup operation, what are the correct sequence of steps after the backup server initiates the scheduled backup process?

Question 28
What is an example of an active attack on an IT infrastructure?
Question 29
Which LUN expansion technique provides both capacity expansion and performance improvement?
Question 30
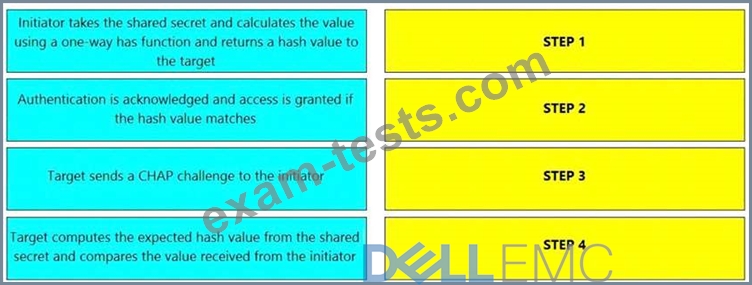
What is the correct sequence of steps to authenticate an initiator and a target using one-way Challenge Handshake Authentication Protocol (CHAP) after the initiator performs a login to the target?