Question 96
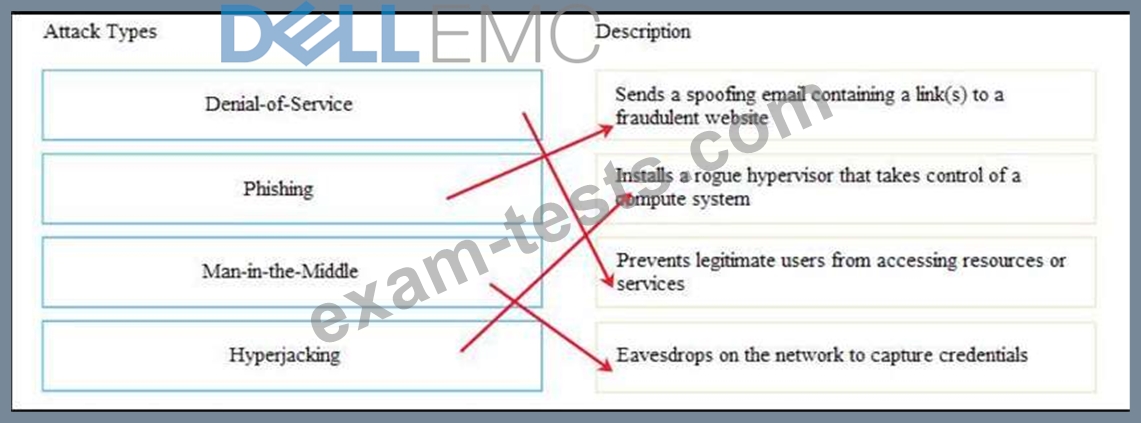
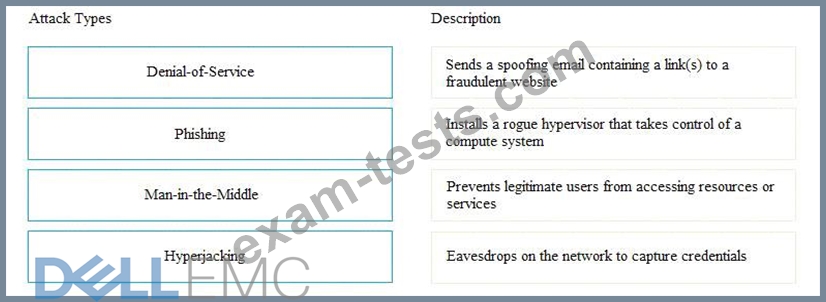
Match the types of attack with their respective description.

Question 97
Drag and Drop Question
If the client requests authorization from the resource owner, what are the remaining sequence of steps to authenticate a user using OAuth control?

If the client requests authorization from the resource owner, what are the remaining sequence of steps to authenticate a user using OAuth control?

Question 98
What is an accurate statement about a software RAID implementation?
Question 99
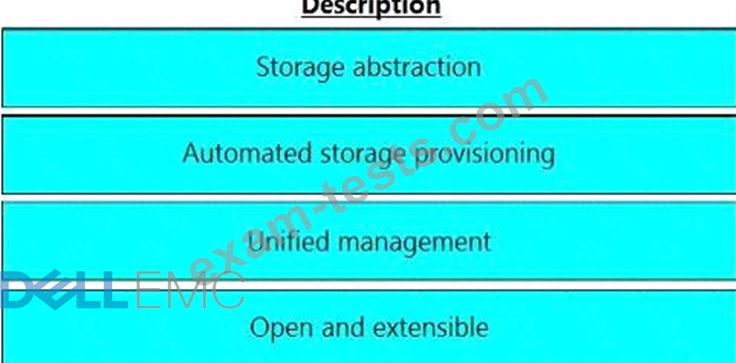
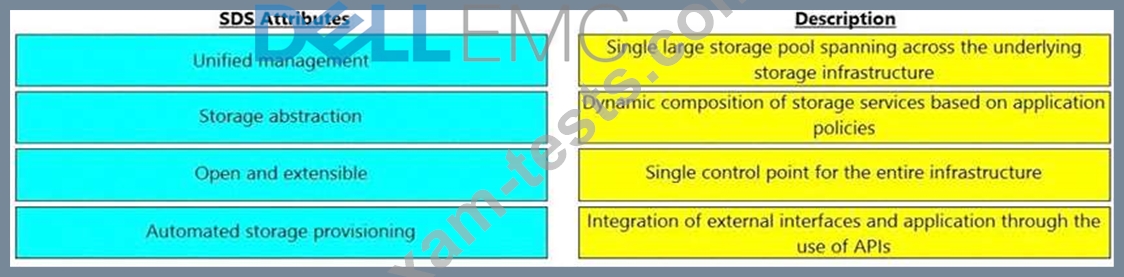
Match the software-defined storage (SDS) attributes with their respective description.

Question 100
Which management function involves configuring LUN masking to restrict hosts from accessing a specific LUN in a data center environment?