Question 76
Which technique is used in Kerberos to authenticate a client-server application across an insecure network?
Question 77
Based on the exhibit,
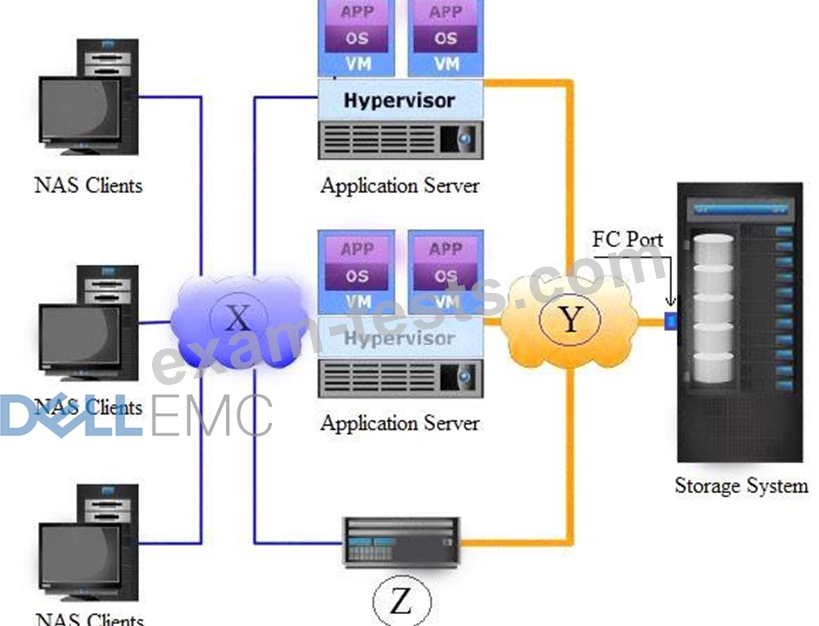
what does the "X", "Y", and "Z" represent in a NAS environment?

what does the "X", "Y", and "Z" represent in a NAS environment?
Question 78
What is determined based on the recovery point objective in an asynchronous remote replication?
Question 79
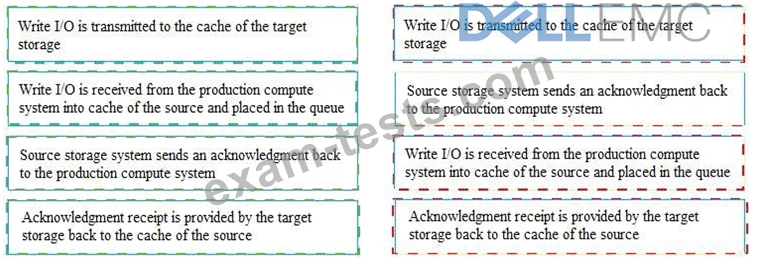
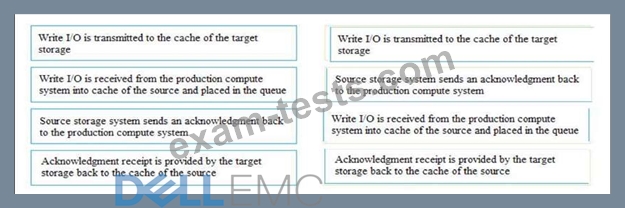
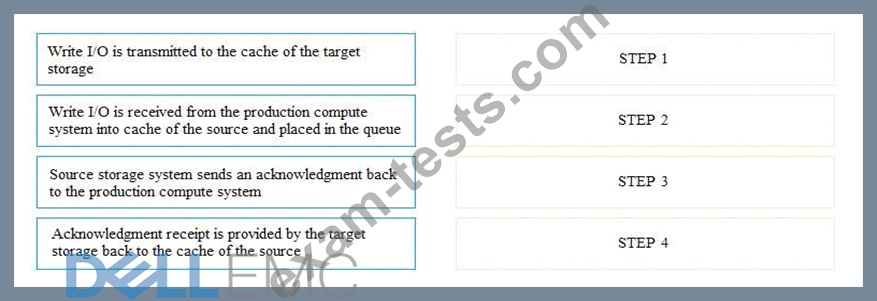
What is the correct sequence of steps that need to be performed in storage system-based synchronous remote replication?

Question 80
What is a benefit of using content addressed storage (CAS) as an archival solution?