Question 11
What is the first step suggested before implementing any single CIS Control?
Question 12
To effectively implement the Data Protection CIS Control, which task needs to be implemented first?
Question 13
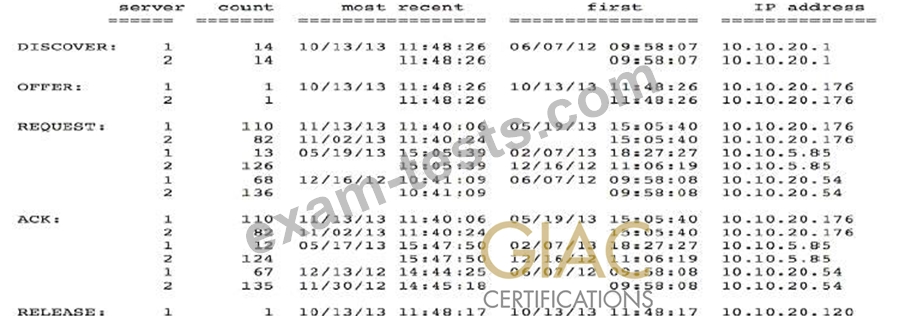
Acme Corporation performed an investigation of its centralized logging capabilities. It found that the central server is missing several types of logs from three servers in Acme's inventory. Given these findings, what is the most appropriate next step?
Question 14
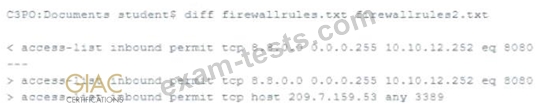
Which of the following actions produced the output seen below?

Question 15
DHCP logging output in the screenshot would be used for which of the following?