Question 26
Given the audit finding below, which CIS Control was being measured?
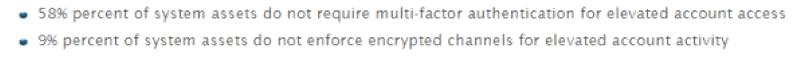

Question 27
Which of the following CIS Controls is used to manage the security lifecycle by validating that the documented controls are in place?
Question 28
Which of the following statements is appropriate in an incident response report?
Question 29
An organization wants to test its procedure for data recovery. Which of the following will be most effective?
Question 30
When evaluating the Wireless Access Control CIS Control, which of the following systems needs to be tested?

