Question 181
Which of the following threats is a combination of worm, virus, and Trojan horse characteristics?
Question 182
Victor works as a professional Ethical Hacker for SecureEnet Inc. He wants to scan the wireless network of the company. He uses a tool that is a free open-source utility for network exploration. The tool uses raw IP packets to determine the following:
* What ports are open on our network systems.
* What hosts are available on the network.
* Identify unauthorized wireless access points.
* What services (application name and version) those hosts are offering.
* What operating systems (and OS versions) they are running.
* What type of packet filters/firewalls are in use.
Which of the following tools is Victor using?
* What ports are open on our network systems.
* What hosts are available on the network.
* Identify unauthorized wireless access points.
* What services (application name and version) those hosts are offering.
* What operating systems (and OS versions) they are running.
* What type of packet filters/firewalls are in use.
Which of the following tools is Victor using?
Question 183
Which of the following Trojans is used by attackers to modify the Web browser settings?
Question 184
Which of the following refers to applications or files that are not classified as viruses or Trojan horse programs, but
can still negatively affect the performance of the computers on your network and introduce significant security risks
to your organization.
can still negatively affect the performance of the computers on your network and introduce significant security risks
to your organization.
Question 185
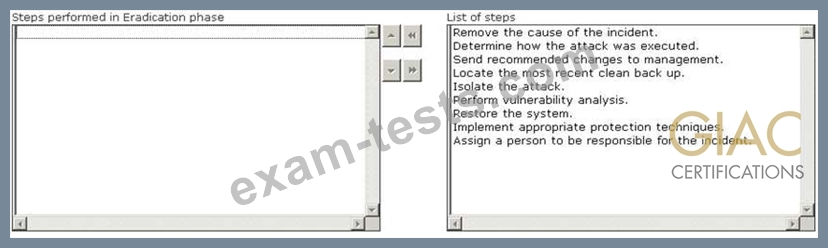
Choose the correct actions performed during the Eradication step of the incident handling process.

Premium Bundle
Newest GCIH Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing GCIH Exam! BraindumpsPass.com now offer the updated GCIH exam dumps, the BraindumpsPass.com GCIH exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com GCIH pdf dumps with Exam Engine here:


