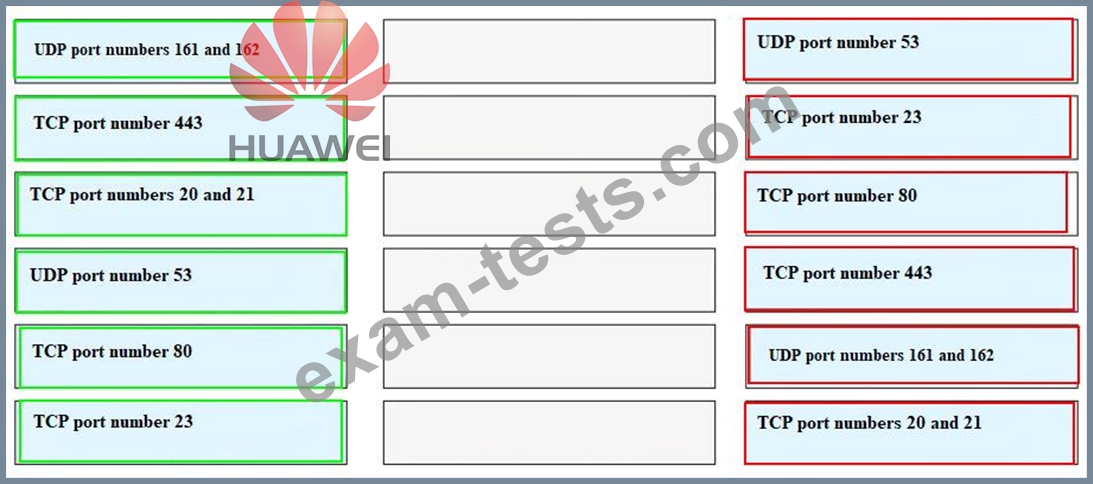
Question 16
Match each of the following application layer service protocols with the correct transport layer protocols and port numbers.


Question 17
The RADIUS protocol specifies how to pass user information, billing information, authentication and billing results between the NAS and the RADIUS server, and the RADIUS server is responsible for receiving the user's connection request, completing the authentication, and returning the result to the NAS.
Question 18
What is correct in the following description of Security Alliance in IPSec?
There are two ways to set up an IPSec SA
There are two ways to set up an IPSec SA
Question 19
In the authentication policy of the firewall, _____ allows the user to not need to enter the user name and password, but can obtain the corresponding relationship between the user and the IP, so as to carry out policy management based on the user[fill in the blank]*
Question 20
The network environment is becoming more and more complex, and network security incidents occur frequently. While accelerating the construction of informatization, enterprises must not only resist external attacks, but also prevent internal management personnel from being involved in data leakage and operation and maintenance accidents due to operational errors and other issues. Which of the following options might reduce operational risk?